Google Workspace Configuration
Background
Twingate integrates with Google Workspace in order to synchronize user accounts, delegate user authentication to Google, and optionally enable group synchronization.
User and group synchronization are performed using the Google Workspace Directory API, authorized via OAuth. In order to enable synchronization, an admin must authorize Twingate to access user and group information for your Google Workspace domain. This connection is initiated from the Identity Provider subsection of Settings in the Twingate Admin Console.
Google Workspace API permissions
Twingate requires the permission to read Google Workspace groups to function, even if you do not choose to enable Group Sync. (Group Sync is disabled by default.)
Steps to configure the Google Workspace Twingate integration
- Enable the Google Workspace integration in Twingate and sign in to your Google Workspace domain.
- Configure the Twingate application in the Google Workspace Admin Console and enable user and group sync.
User Authentication
Twingate delegates user authentication to Google. The user’s email address must match the Google Workspace domain or domains you have configured for access to be authorized. Users without an address matching your configured domain or domains will not be able to authenticate and use Twingate.
This domain restriction also applies to admin users of the Twingate Admin Console. Additional admin users can be set within the Twingate Admin Console.
Multiple domains
Twingate supports multiple domains configured as part of the same Google Workspace account. You may add additional domains by going to Settings > Identity Provider and selecting ”+ Add Domain” in the Google Workspace settings.
You will only be able to add domains that have already been configured and authorized in Google Workspace. See the Google Workspace documentation for more information.
Google Workspace sync with Twingate
The Google Workspace Directory API does not currently provide capabilities for real-time sync for groups and OUs. Only user changes are updated in real-time, received via webhook updates. The current polling period for groups and OUs depends on your plan.
For the Starter plan, groups and OUs are synced every 24 hours.
For the Teams, Business, and Enterprise plans, groups and OUs are synced every two hours.
The “Manually Sync Now” option in the Google Workspace ⋯ action menu will schedule the sync to start immediately, but it may still take several minutes for sync to completed.
User Sync
Only users that are active in your Google Workspace domain will be able to sign in to your Twingate Network. Inactive users will also be synced, but will be marked as inactive in Twingate and unable to sign in. Once synced, users can be given access to Twingate Resources based on Group membership.
Group and Organizational Unit Sync
By default, Google Workspace Group and Organizational Unit (OU) sync is disabled. If you would like Twingate to sync groups or OUs, edit the Identity Provider sync settings via the ⋯ action menu.
Disabling Group or OU Sync will affect synced groups and OUs. How synced groups and OUs are treated depends on whether Selective Sync is enabled:
- If Selective Sync is disabled, all groups and OUs that have access to a Resource will be converted into a Twingate Group. Groups and OUs that do not have access to any Resources will be deleted.
- If Selective Sync is enabled, all groups and OUs, even if they have access to a Resource, will be deleted.
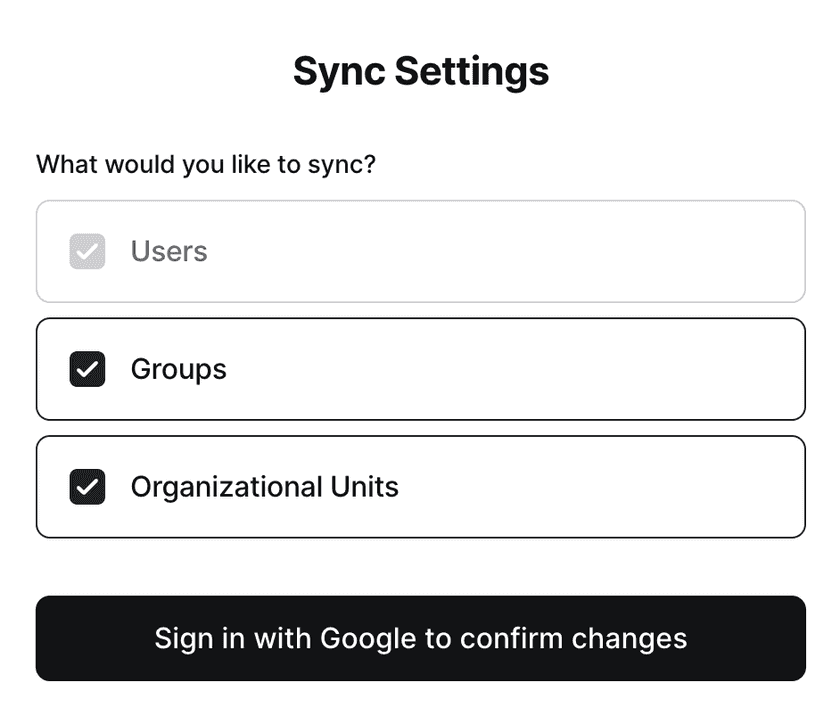
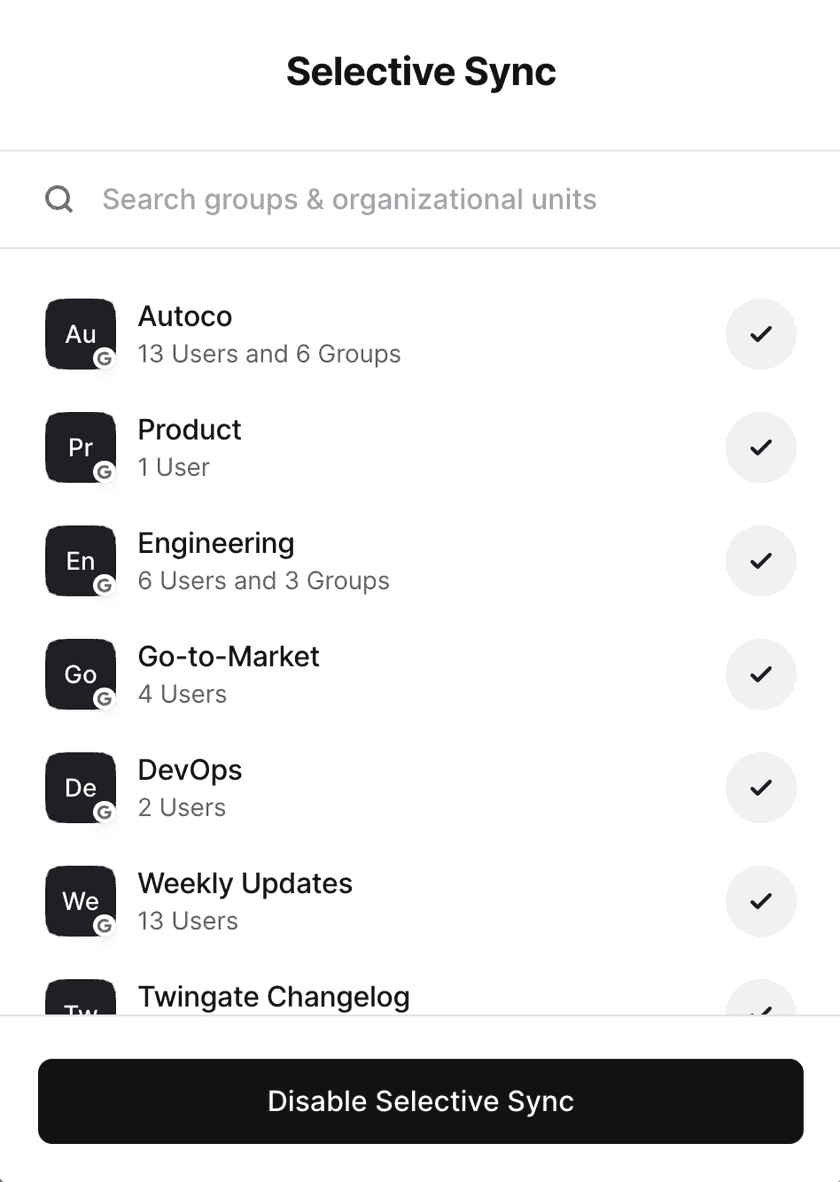
Selective Sync
Enabling Selective Sync will limit which Google Workspace users, groups and OUs Twingate syncs. To enable Selective Sync, enable syncing groups, OUs, or both via the ⋯ action menu. Next, click on the “Manage Selection” button in the “Selective Sync” panel.
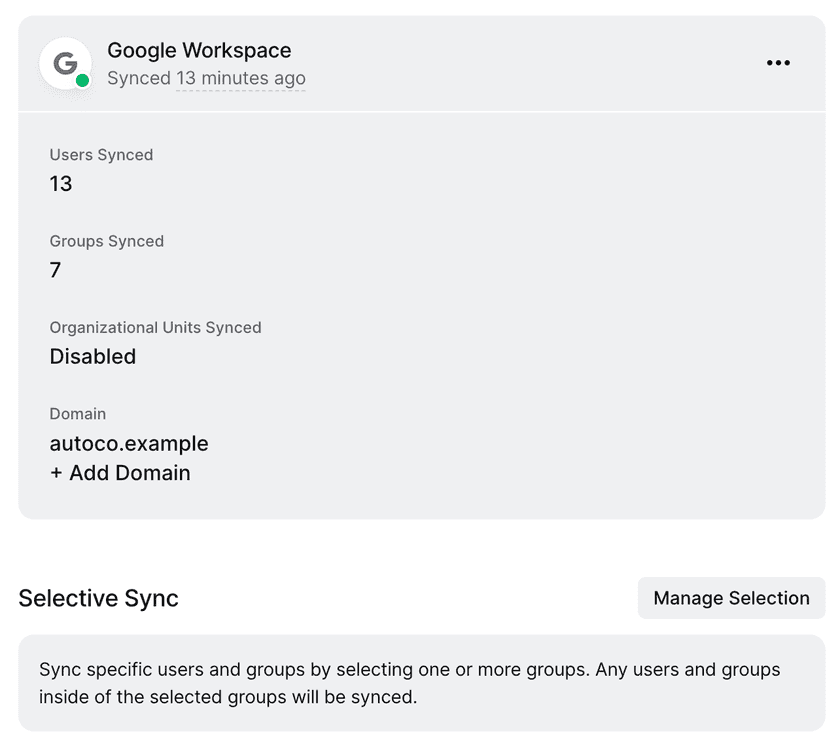
Select which groups and OUs you want Twingate to sync.
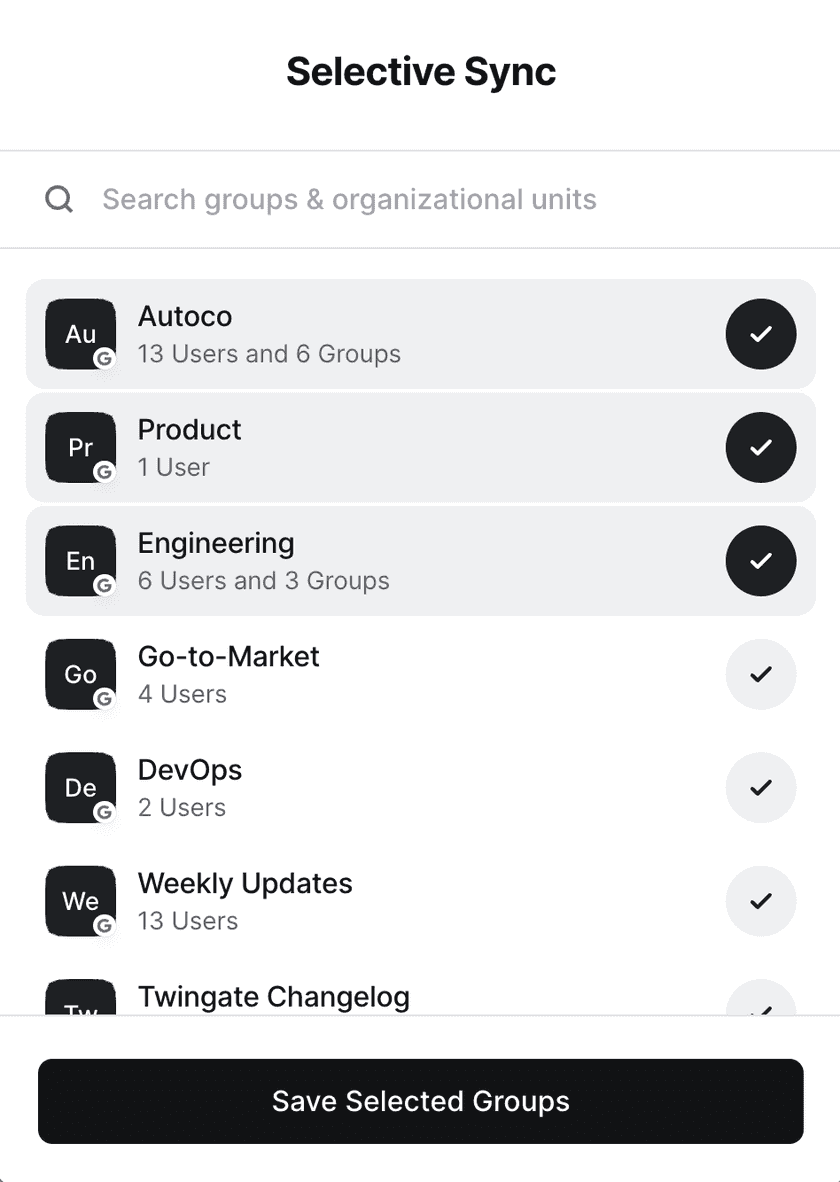
Once your selection is saved, your selection will be used when the next sync happens. Twingate will sync all selected groups, the children of selected groups, and all users in synced groups. Twingate will not sync groups and OUs that are not selected and are not children of selected groups. Likewise, users not in synced groups will not be synced.
To change which groups and OUs Twingate syncs, click on the “Manage Selection” button. When groups and OUs are deselected, they will be deleted even if they have access to Resources.
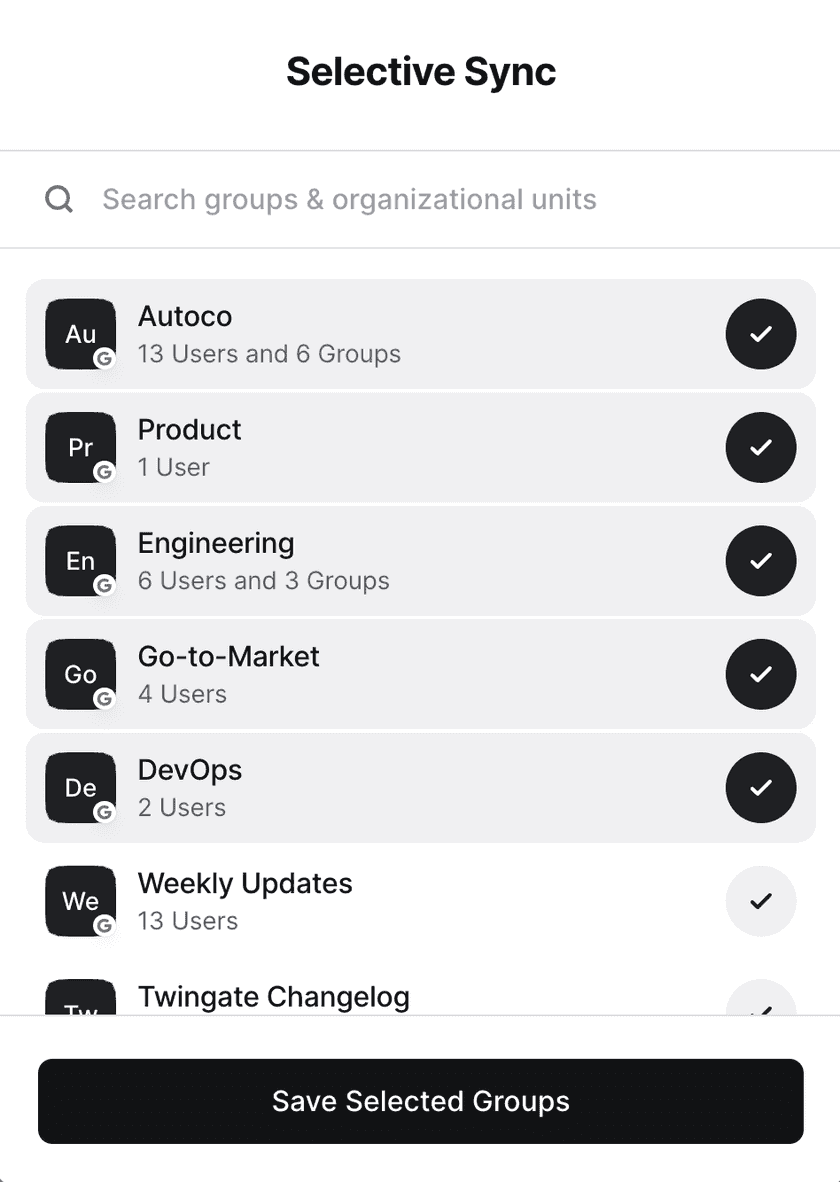
To disable Selective Sync, click on the “Manage Selection” button and deselect all groups. When Selective Sync is disabled, all users, group and OUs will be synced.
Be sure to sync your own account!
When selecting which groups and OUs are sync, be sure to include at least one group that includes your own account. If you accidentally omit your own account from Selective Sync, have another admin add you or reach out to via the Help Center.
Permissions
User and group synchronization is performed via the Google Workspace API. In order to enable synchronization, an admin must authorize Twingate to access user and groups information for your Google Workspace domain. This is done from the Identity Provider subsection section of Settings in the Twingate Admin Console.
Minimum admin permissions
The user authorizing user sync must have one of the following admin roles in G Suite:
- A Super Admin
- A Groups Admin
- A User Management Admin
- A Help Desk Admin
- A custom admin role with at least a “Users: Read” and “Groups: Read” permissions under the Admin API.
(More information on Google Workspace administrator roles can be found in Google’s Help Center.)
API access control
If attempts to authorize Twingate access to your Google Workspace account fail with an authorization error, you likely have restricted access to third party applications. You can verify this in the Security > API Controls > Manage Google Services section of your Google Workspace admin console, by checking if Google Workspace Admin is listed as a Restricted.
In order to complete the process of connecting Twingate to Google Workspace, there are two options:
- Change Google Workspace Admin to Unrestricted
- In Security > API Controls > Manage Third-Party App Access, find Twingate and click Change access. Select Trusted: Can access all Google services and click Change.
Data privacy
Twingate only syncs the information that is necessary to provide our service:
- User first and last names
- User email addresses
- User avatars
- Group membership (if Group Sync is enabled)
Last updated 6 months ago