Internet Security Client Configuration
When Internet Security is enabled, it’s recommended to configure your Clients to always run Internet Security, even when a user is signed out. Without any configuration, Internet Security features like DNS filtering are only enabled when a user is signed in to the Twingate Client. Setting up Internet Security Client Configuration will ensure that these features are always running.
Additionally, when the Client is configured for Internet Security, users will not be able to quit, sign out of, or switch Networks on the Client.
Minimum Client Versions
Internet Security Client Configuration requires the following Client versions:
- macOS standalone 2024.17 and newer
- Windows 2024.028 and newer
- Linux 2024.018 and newer
Only the macOS standalone app supports this configuration. The macOS App Store client does not support this configuration.
Setting up Internet Security Client Configuration
To enable Internet Security features when users are signed out, you will need to deploy a Machine Key to your end-users’ machines. Additionally, your MDM, e.g. Kandji or Intune, can be used to keep the Twingate Client running all the time.
Machine Keys are currently shared between devices and a single key can be deployed to all of your devices. You can use multiple keys to manage key rotation or to have different keys for different groups of users. Each device uses a single Machine Key.
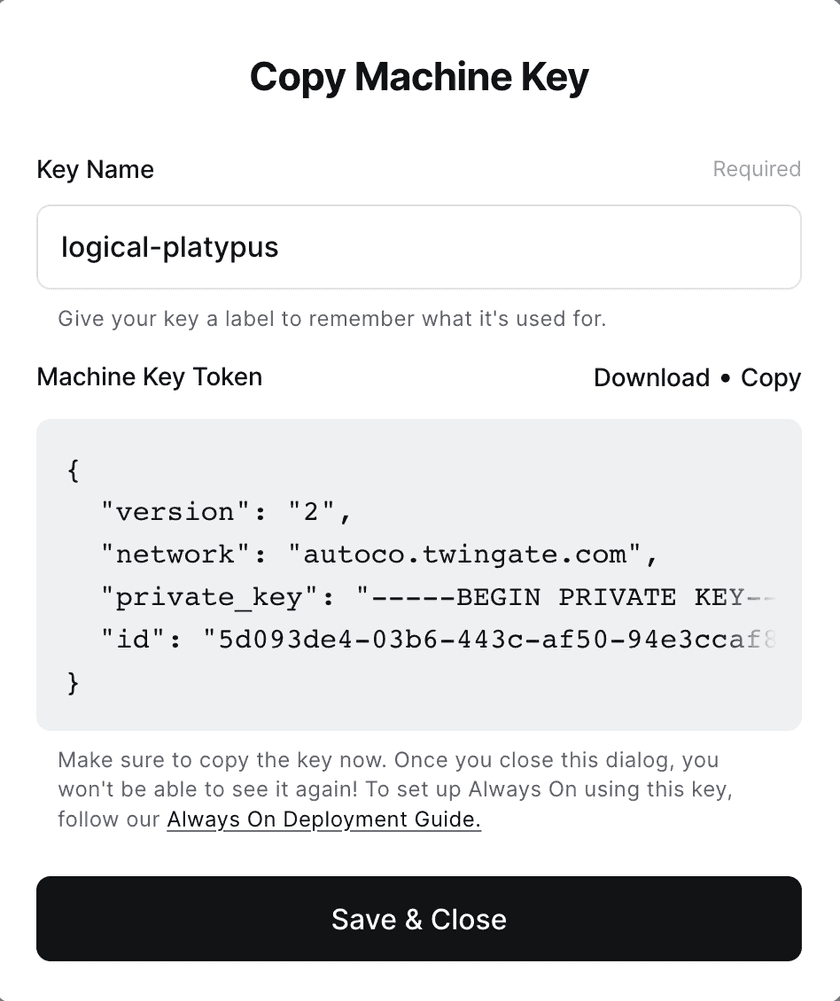
Generating a Machine Key
To generate a Machine Key, navigate to the “Internet Security” tab in the Admin Console, then navigate to the “Client Configuration” sub-tab. Clicking the “Generate Key” button will generate a new Machine Key. Up to 10 keys can be generated at once.
Deploying Machine Keys
Deploy your Machine Keys using your MDM to the following paths:
- macOS:
/Library/Application Support/Twingate/machinekey.conf - Windows:
%ProgramData%/Twingate/machinekey.conf - Linux:
/etc/twingate/machinekey.conf
Machine Key Name
After generating the machine key, ensure that the file is renamed to machinekey.conf before deployment. Using the correct file name is essential for keeping DNS filtering running when Clients are signed out.
Keeping the Twingate Client running
It’s highly recommended to deploy additional configuration via your MDM to keep the Twingate Client running. With just the Machine Key, it’s possible for the Twingate Client to stop running, for example if a user manually closes it via Task Manager (Windows), Activity Monitor (macOS), or the command line (all platforms). By deploying the following configuration via your MDM, Twingate will automatically restart if it quits. This ensures that Internet Security features will truly be running all of the time.
macOS
For macOS, we recommend creating a KeepAlive Launch Agent as follows:
- Create a plist file using the xml example below.
- Name the file:
com.twingate.macos.plist - Save the file to the following location:
/Library/LaunchAgents/com.twingate.macos.plist - Optionally, set the system immutable flag on the file with the following command:
sudo chflags schg /Library/LaunchAgents/com.twingate.macos.plist - Either restart the device or load the Launch Agent to take effect.
<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"><plist version="1.0"><dict> <key>Label</key> <string>com.twingate.macos</string> <key>Program</key> <string>/Applications/Twingate.app/Contents/MacOS/Twingate</string> <key>KeepAlive</key> <true/> <key>RunAtLoad</key> <true/></dict></plist>Windows
For Windows, we recommend using an Intune proactive remediation
# Detection script$twingate = Get-Process twingate -ErrorAction SilentlyContinueif ($twingate) { Write-Host "Twingate is running" exit 0}Write-Host "Twingate is not running"exit 1# Remediation scriptWrite-Host "Restarting Twingate"Start-Process -FilePath "C:\Program Files\Twingate\Twingate.exe"FAQ
Will setting up Internet Security Client Configuration also set up DNS filtering?
No. DNS filtering is set up independently from Internet Security Client Configuration. To learn more about DNS filtering and other Secure DNS options, ready our Internet Security documentation.
Why isn’t my device showing up before a user has signed in?
Devices will not show up in the Admin Console until a user has signed in for the first time. While deploying a Machine Key will enable DNS filtering before a user signs in, their device will not show up in the Admin Console until they sign in for the first time.
Why am I not seeing a device name for signed out devices?
Signed out devices have slightly different DNS filtering logs. See the DNS filtering documentation for more information.
Last updated 1 year ago