DNS Filtering
Availability
DNS filtering is available as an add-on for the Business and Enterprise plans.
DNS filtering
Twingate provides native DNS filtering capabilities for every user in your Twingate Network running the macOS, Windows, or Linux Client. DNS filtering uses DNS-over-HTTPS (DoH). See the DoH documentation for more information on what options are available for secure DNS.
Mobile Devices
At this time, DNS filtering is only available on macOS, Windows, and Linux Client platforms.
Just like DoH, Twingate DNS filtering will intercept and filter all DNS traffic with no configuration changes required other than running the Twingate Client.
DNS filtering gives you the ability to control what websites your users can access. By default, DNS filtering will automatically protect your users from a wide range of potential security threats, blocking sites known to host phishing, distribute malware, and more.
Additionally, you can use DNS filtering to restrict what kinds of content your users can access, restricting access to things ranging from unauthorized SaaS apps to websites not appropriate for work.
How DNS filtering works
DNS (the Domain Name System) is a distributed system used to associate domains like twingate.com with IP addresses like 203.0.113.42. DNS servers store DNS records, which are the mappings from a domain name to an IP address (in addition to other kinds of information).
When using Twingate DNS Filtering, you’re connected to Twingate’s DNS servers. In addition to answering DNS queries, Twingate will block queries for blocked websites. For example, if evil.example is blocked, a user trying to access evil.example won’t find a matching IP address and, consequently, won’t be able to visit the domain.
Since DNS filtering works on the DNS layer, all kinds of traffic, e.g. HTTPS traffic, SSH connections and more, will be blocked from blocked domains.
Block pages
When a domain is blocked and the user is viewing it in a browser, Twingate will redirect the user to a block page. The block page identifies why a domain was blocked, making it easier for users to understand the reason for the block and, if needed, to troubleshoot a blocked domain.
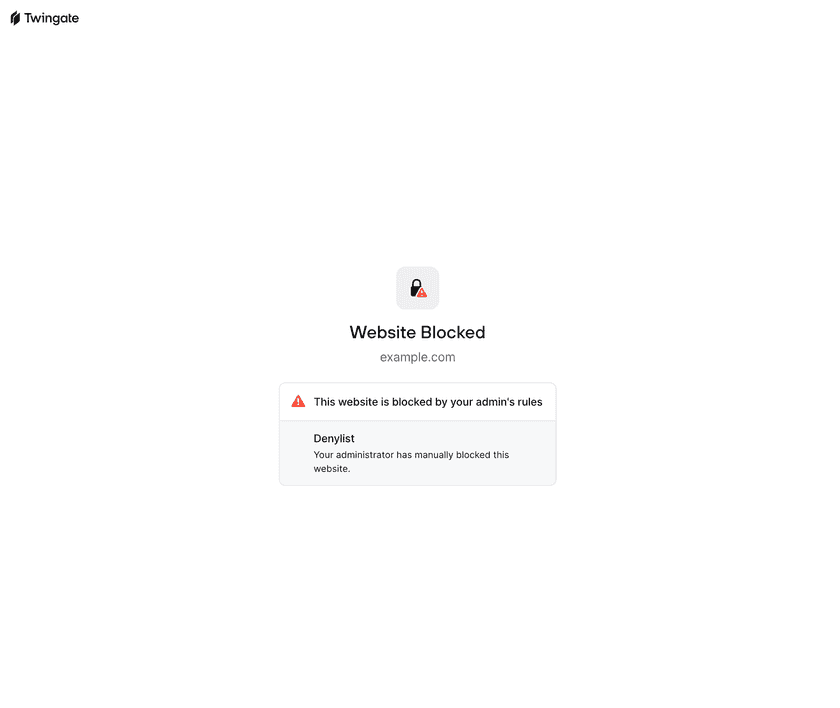
By default, the block page works for sites accessed via HTTP. To have block pages show up when accessing a site via HTTPs, deploy the Twingate Browser Extension to your users’ browsers.
Enabling DNS filtering
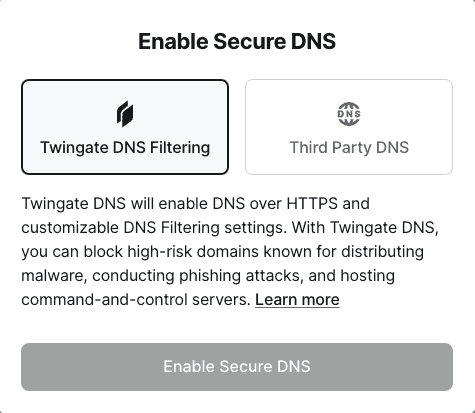
To enable DNS filtering, navigate to the “Internet Security” tab in the Admin Console. If Secure DNS is disabled, enable Secure DNS and choose “Twingate DNS Filtering”. If Secure DNS is already enabled, change your DNS-over-HTTPS resolver to “Twingate DNS Filtering”.
DNS filtering profiles
DNS filtering rules are configured via DNS filtering profiles. Each profile has a set of rules and can have any number of Groups assigned to it. The specific rules that admins can configure are detailed below. When a Group is assigned to a profile, the users in that Group will use the profile they are assigned to. As a user can belong to multiple Groups, profiles are ranked, with profiles towards the top of the list taking priority over any profiles below it. If a user does not belong to any Groups assigned to a DNS filtering profile, their DNS traffic will not be filtered.
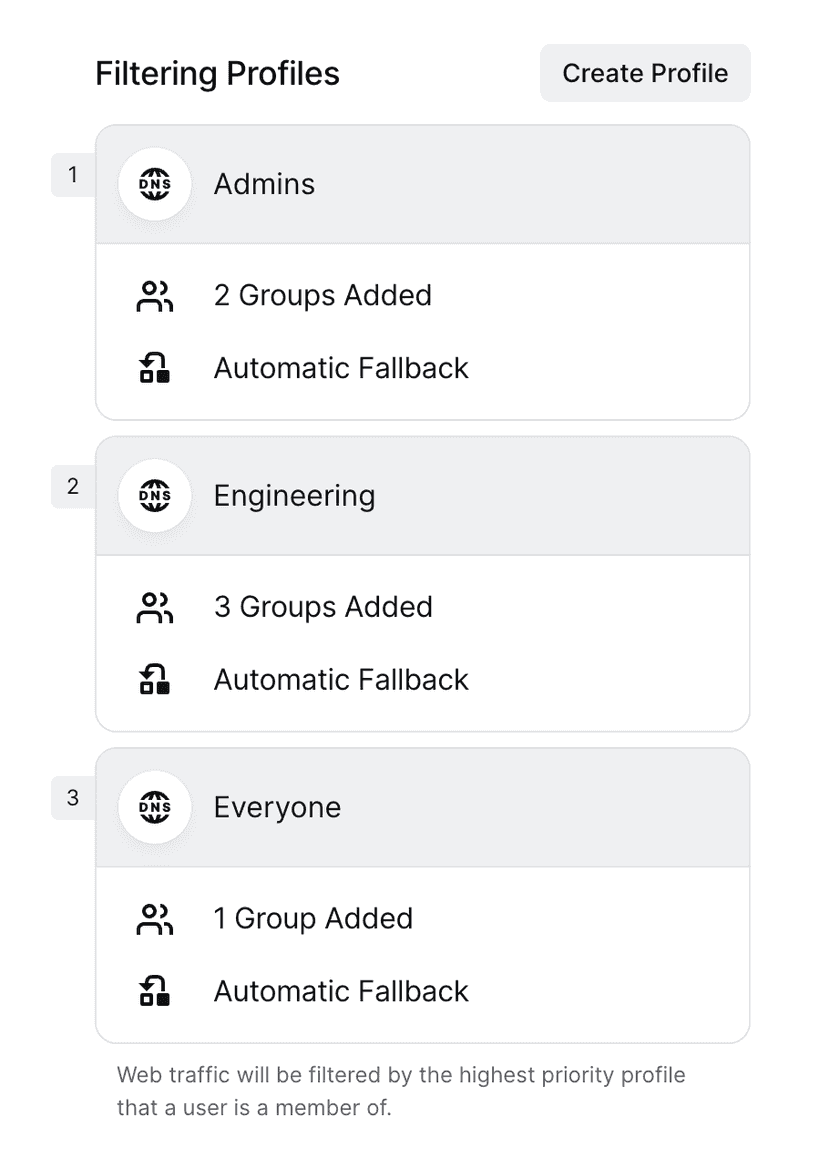
By default, a single profile is created and the Everyone group is assigned to it. Admins can optionally limit DNS filtering to a specific set of Groups by removing the Everyone group and assigning other Groups in its place.
It’s recommended, but not required, to have a “default” DNS filtering profile by creating one ranked below all other profiles and assigning the Everyone group to it.
Groups can only be assigned to a single DNS filtering profile at one time. Similarly, Groups cannot be both assigned to a profile and excluded from DNS filtering at the same time. Exception Groups take precedence over Enrolled Groups, e.g. if a user is in an enrolled Group and an Excluded one, the user will not have DNS filtering enabled.
When a device is configured to always run Internet Security and is signed out, it will use the lowest ranked DNS filtering profile.
There is a limit of 10 DNS filtering profiles.
Configuring DNS filtering rules
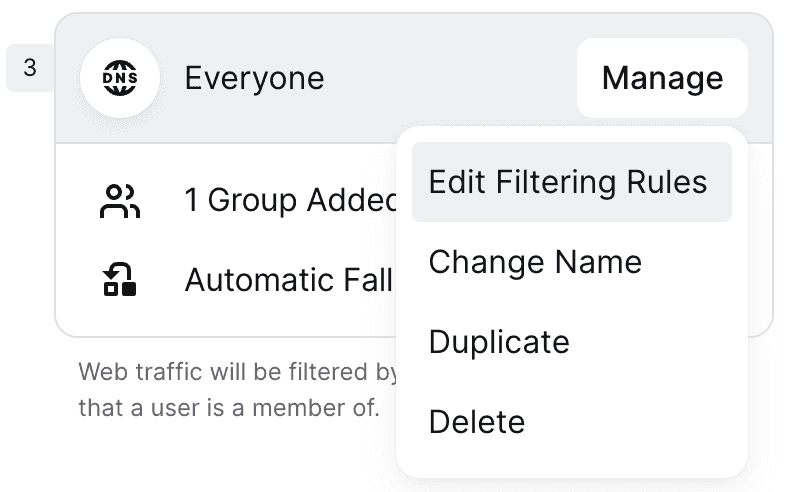
To configure DNS filtering rules, click on a profile’s name or click on the “Manage” button followed by “Edit Filtering Rules”. Other settings, like assigned groups or fallback method, can be configured similarly.
Allowing and blocking specific domains
Domains can be allowed and blocked by adding them to the allowlist and denylist respectively. TLDs can be added to the denylist to block all domains with a given TLD. For example, adding .zip to the denylist would block domains like 1.zip, exe.zip, and similar domains.
In the filtering rules modal, add and remove domains from the allowlist and denylist as needed.
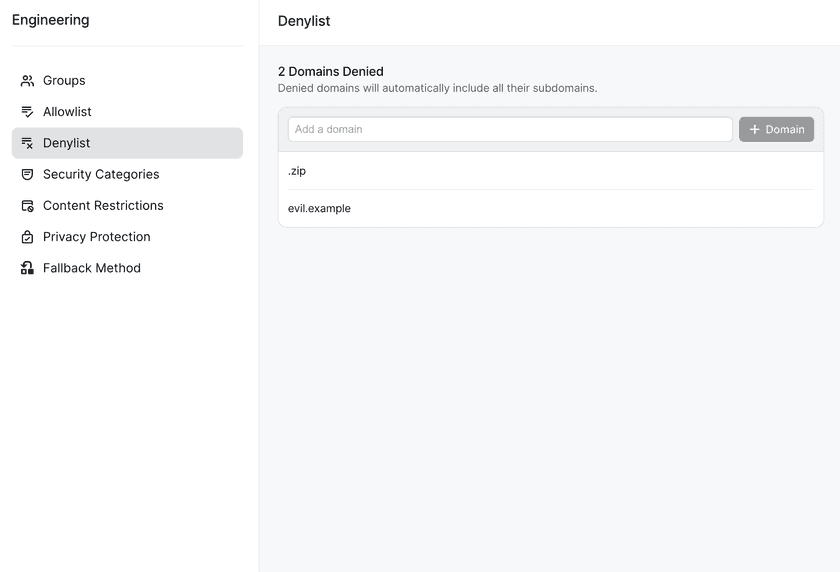
The allowlist takes precedence over all other filtering rules, i.e. domains added to the allowlist will not be blocked even if another rule would otherwise block them.
Blocking security threats
Twingate has the ability to block the following categories of security threats:
- Threat Intelligence Feeds - includes domains hosting malware, phishing, and more.
- Google Safe Browsing - includes malicious domains flagged by Google Safe Browsing.
- DNS rebinding - includes domains that return IP address in private IP ranges.
- IDN homograph attacks - includes domains that use homoglyphs, e.g. substituting the Cyrillic “е” for the Latin “e”.
- Typosquatting - includes domains that use typos of popular domains.
- Domain generation algorithms - includes generated domains used to host malicious content.
- Newly registered domains - includes domains registered within the last 30 days.
- Parked domains - includes parked domains that may be hosting malicious content.
To configure which categories are enabled, click on “Security Categories” to open up the configuration modal. By default, all categories except newly registered domains are enabled.
Blocking content categories
Content categories are a quick way to block many domains based on the content that they host. Twingate can block the following content categories:
- Gambling - includes domains that host content related to gambling.
- Dating - includes dating websites.
- Adult content - includes sexually explicit and other adult content.
- Piracy - includes content related to piracy and copyright-infringement.
- Social media - includes social media sites, but does not include messaging apps.
- Games - includes online gaming websites and applications.
- Streaming sites - includes streaming sites like YouTube, Netflix, and more.
- Force Safe Search - forces safe search on major search engines and blocks search engines where safe search cannot be forced.
- YouTube safe mode - forces YouTube safe mode to block mature videos.
To configure which content categories are filtered, click on “Content Restrictions” to open up the configuration modal.
Add privacy protection
Twingate can also provide a layer of privacy protection via DNS filtering. Currently, the following options are available:
- Block disguised third-party trackers - blocks disguised third-party trackers that disguise themselves as first-party trackers.
- Block affiliate & tracking links - blocks affiliate and tracking domains common on monetized websites and emails. Note that blocking tracking links may make it harder to interact with or unsubscribe from emails as many email links are tracking links.
- Block ads and trackers - blocks ads and (non-disguised) trackers using regularly updated and exhaustive lists.
To configure privacy protection, click on “Privacy Protection” to open up the configuration modal. Note that blocking ads, trackers, and tracking links may lead to certain sites not functioning as expecting.
DNS filtering logs
Filtering Analytics
Filtering analytics shows a 90 day, 30 day, or 7 day summary of your DNS filtering activity, including the total number of DNS queries, the number of blocked queries, and the percentage of queries that were blocked.
Recent DNS Activity
Recent DNS activity shows a log of recent DNS filtering events. Logs can be quickly filtered to show all activity, which includes allowed and blocked domains, and just blocked domains. Clicking into an event will show more details, including the device’s hostname and IP address, the filtering profile used, and, if a domain was blocked, the reason for a domain being blocked.
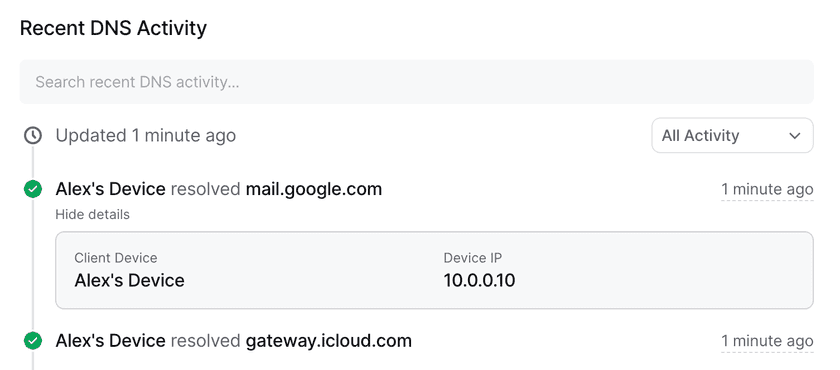
Signed out device analytics
Devices can still use DNS filtering, even if a user is signed out, if they’ve been configured to run DNS filtering all of the time. If a user is signed out, their DNS filtering logs will show one of three things:
- If the device has never signed into Twingate, you will see its hostname in the DNS filtering logs.
- If the device has signed into Twingate and only one user has ever used that device, you will see the Twingate device name in the DNS filtering logs.
- If the device has signed into Twingate and been used by multiple users (e.g. a multi-user device or a laptop that was used by a former colleague), you will see the name of the most recently signed in Twingate device in the DNS filtering logs.
Older Client versions
Client versions prior to macOS 2024.311 or Windows 2024.351 will show more generic device information when the user is signed out. In particular, you may see “No hostname” or “No device”. Upgrade your users’ Clients to see the hostname in the DNS filtering event feed.
Syncing DNS filtering logs to S3
DNS filtering logs can be synced to AWS S3 buckets. The logs can then be processed or sent to a SIEM, providing real time visibility into DNS filtering activity and enabling advanced analytics within your SIEM. To learn more, read our documentation on syncing data to S3.
DNS Filtering events synced to AWS S3 buckets are exported in JSON. Each event is represented as a single line. They come in the following format:
{ "event_type": "dns_filtering", "event": { "version": 1, "time": "2024-11-28T00:21:28.165017+00:00", // UTC datetime of event "domain": "img.youtube.com", // domain that was submited "root": "youtube.com", // root of domain "device": { "id": "RGV2aWNlOjQ5NTY2Ng==", // if device has ever logged in then Twingate device id, otherwise hardware id "name": "User's Device" // if device is logged in then Twingate device name, otherwise blank }, "connection": { "client_ip": "111.222.111.222", // device client IP address "protocol": "DNS-over-HTTPS" }, "status": "default", // "default" for a successful lookup, "blocked" if any category or denylist entry matched, "allowed" if an allow list entry matched "reasons": [] }}{ "event_type": "dns_filtering", "event": { "version": 1, "time": "2024-11-28T00:21:33.476841+00:00", // UTC datetime of event "domain": "www.reddit.com", // domain that was submitted "root": "reddit.com", // root of domain "device": { "id": "RGV2aWNlOjQ5NTY2Ng==", // if device has ever logged in then Twingate device id, otherwise hardware id "name": "User's Device" // if device is logged in then Twingate device name, otherwise blank }, "connection": { "client_ip": "111.222.111.222", // device client IP address "protocol": "DNS-over-HTTPS" }, "status": "blocked", // "default" for a successful lookup, "blocked" if any category or denylist entry matched, "allowed" if an allow list entry matched "reasons": [ { "id": "category:social-networks", "name": "Social Networks" } ] }}FAQ
How do I know if a domain is blocked by DNS filtering?
Blocked domains can be viewed in the “Recent DNS Activity” logs on the Secure DNS page. You can filter the DNS filtering logs for just blocked events to quickly see which domains have been blocked.
For end users, domains that are blocked by DNS filtering will not be accessible to users running the Twingate Client when DNS filtering is enabled. A blocked domain will behave the same as a domain that doesn’t exist. For example, if blocked.example is blocked, opening it in a web browser will result in an error that the site can’t be reached.
How can I allow users to access a blocked domain?
If a domain is blocked and it shouldn’t be, add that domain to the allowlist.
How do I keep DNS filtering running all of the time for my users?
By default, DNS filtering will run whenever a user is signed into the Twingate Client. To keep DNS filtering running all the time, even when no user is signed in, set up Internet Security Client Configuration.
How do I turn off DNS filtering for a subset of my users?
To disable DNS filtering for a subset of your users, add those users to an Exception Group.
Last updated 11 months ago