Device Administration
Twingate displays the devices your users connect to Twingate from in both the user detail page for an individual user and the Devices tab. On this page, we show information collected from the device, including, but not limited to, the name, make & model, Twingate Client version, posture information, and which Trusted Profiles have been met.
→ For more on Trusted Profiles, see the Device Security Guide.
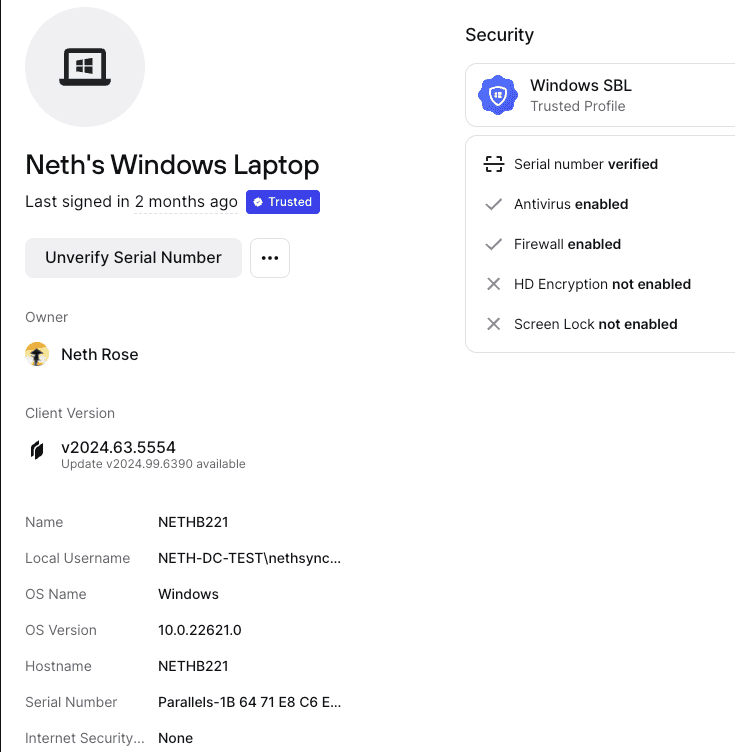
Device Attributes
Some attributes are only supported by certain Client platforms, please see below for details.
| Attribute | Description | Platforms Supported |
|---|---|---|
| Name | The “friendly name” of the device, set by the user. | Windows, macOS, iOS |
| Hostname | The DNS hostname that the device assigns to itself. Often based on the device name. | Windows, macOS, Linux |
| Make | The manufacturer of the device. | macOS, Linux, iOS |
| Model | The model name of the device. | macOS, Linux, iOS |
| OS name | The name of the operating system. | All |
| OS version | The numerical version of the operating system. | All |
| Serial number | The hardware serial number of the device. | Windows, macOS, Linux |
| Local username | The name of the local user running Twingate. | Windows, macOS, Linux |
| Client version | The version of the Twingate Client running on the device. | All |
| Active state | The status of the device. | All |
| Connection indicator | The green dot on the device icon indicates that the user is currently logged in to this device | All |
| Internet Security | The status of the device’s Internet Security configuration | Windows, macOS, Linux |
Verified Devices
Twingate supports various integrations with EDR and MDM software to automatically mark devices as verified. In addition, Twingate allows admins to designate specific devices as manually verified. Verified devices can be incorporated into Security Policies so that this status is taken into account.
This policy requirement can be enforced for any device with the Twingate client app, regardless of platform or location. For information on incorporating device verification into Security Policies, see the Device Security Guide.
Device Active State
Devices in Twingate can have three different states to make device management easier: active, archived, and blocked. These states can be set both in the Admin Console or through the API.
| State | Use cases | Admin Console Visibility | Protected Resource Access |
|---|---|---|---|
| Active | Default state Actively used devices | Visible | Requires sign in |
| Archived | Old or deprecated devices Devices that have not signed in or accessed a Resource in 90 days | Filtered out | Requires sign in |
| Blocked | Lost, stolen, or deprecated devices | Filtered out | No access |
By default, all new devices are in an active state. This means that users on these devices can access protected Resources, provided that they meet the requirements of the relevant Security Policies.
Devices that have not signed in or accessed a Resource in the past 90 days are automatically archived. Alternatively, device states can manually be set to archived. This will automatically sign out the user from the device and will require the user to re-authenticate into the client in order to access protected Resources. Re-authentication will automatically return an archived device to its active state.
For lost, stolen, or deprecated devices, you can set their state to blocked. This will automatically sign out the user from the device. This user will be unable to sign into this device again and the device will lose access to protected Resources.
Last updated 1 year ago