CrowdStrike Configuration
Business & Enterprise only
Note that our Crowdstrike integration is limited to the Business and Enterprise product plans. See our pricing page for more information.
CrowdStrike Zero Trust Assessment feature must be enabled
This integration requires that the CrowdStrike Falcon Zero Trust Assessment feature is enabled, and the CID is shared with CrowdStrike Support. Without this feature, the ZTA score will not be deployed on devices and be unavailable to Twingate to assess the device’s security posture. CrowdStrike customers must ask that this Enterprise functionality be enabled by reaching out to the CrowdStrike customer support team directly to enable the Zero Trust Assessment on your Falcon CID.
Prior to following the steps below you can verify this feature is enabled and third party permission granted, by checking for the contents of the file %ProgramData%\CrowdStrike\ZeroTrustAsssessment\data.zta (Windows) or /Library/Application Support/Crowdstrike/ZeroTrustAssessment/data.zta (macOS) on a CrowdStrike endpoint device to confirm that the ZTA file is being created and is not empty (is not 0KB in size).
Background
Twingate integrates with CrowdStrike so that admins can have it as a requirement to sign in to Twingate or access private resources. When CrowdStrike is selected as a trust method within Device Security, it can be incorporated into Security Policies. Only devices that are verified through the CrowdStrike integration will be considered satisfying the Trusted Profile and thus be allowed to access private resources.
How it works
Twingate integrates with CrowdStrike by utilizing the CrowdStrike API to pull a list of devices managed under a specific customer’s tenant. Additionally, the Twingate client accesses either the Crowdstrike Agent ID on the device or the ZTA file, checking its validity and pulling the unique device identifier. If the device is verified to be managed under the customer’s Twingate client, it will be considered CrowdStrike-verified in Twingate.
Configuring the CrowdStrike integration in Twingate
1. In the CrowdStrike Falcon platform, generate a new API client token
The following scopes are required:
- Hosts: Read
- Zero Trust Assessment: Read
Copy and save the API Client ID and API Client Secret.
2. In Twingate, navigate to Settings and then select Device Settings

3. Select “Connect” next to CrowdStrike
Input your API Client ID, API Client Secret, and the Base URL for your CrowdStrike tenant, which were generated in step 1.
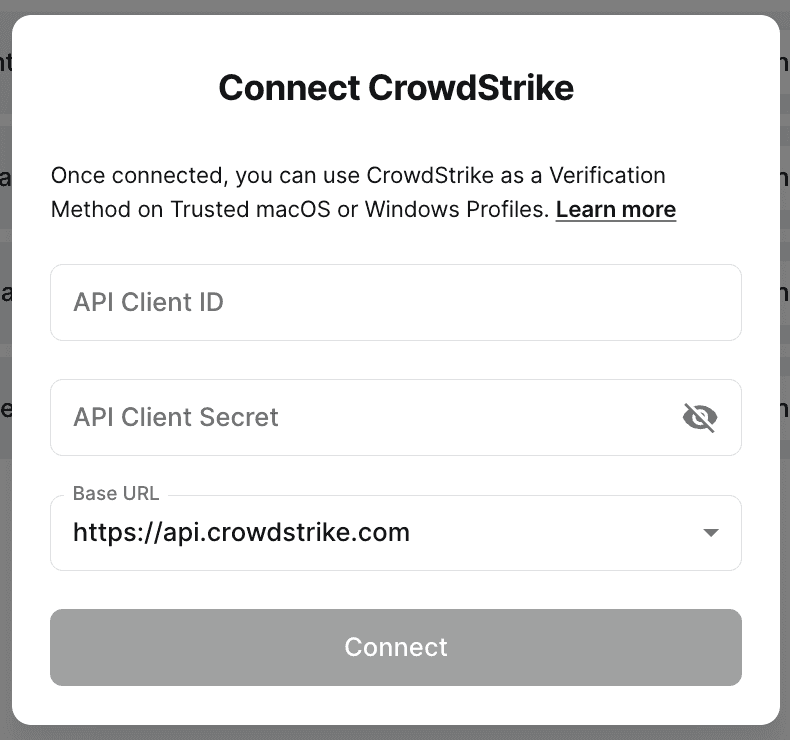
4. The Device Settings page will now show the current status of the integration

Incorporating CrowdStrike into Security Policies
After the CrowdStrike integration has been configured, it can be incorporated into Device Security Trusted Profiles.
For macOS, Windows, or Linux (requires version 2024.018+), create a Trusted Profile and require CrowdStrike as a Trust Method. Only devices that have CrowdStrike configured will satisfy the requirements of this Trusted Profile.
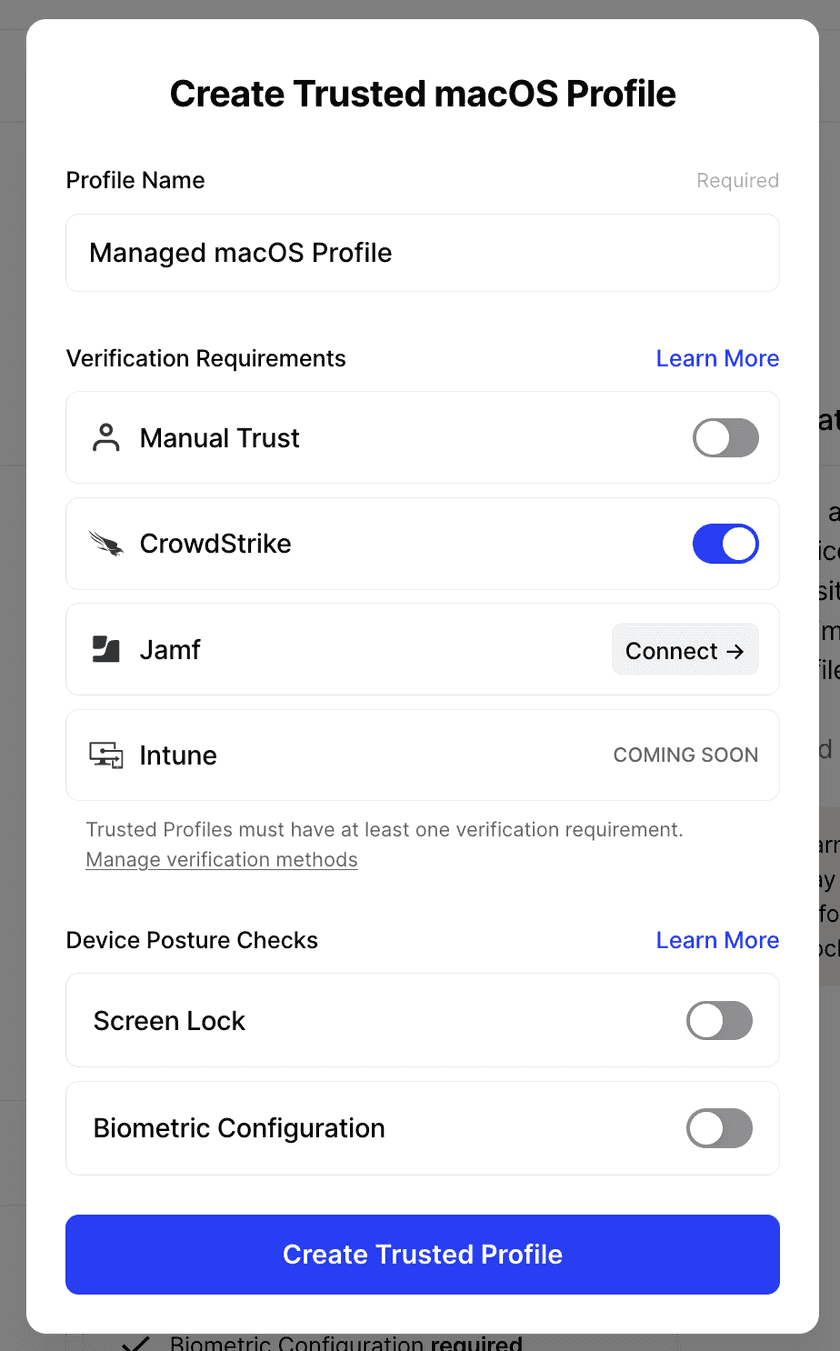
The Trusted Profile can now be incorporated into Security Policies.
Troubleshooting
After the CrowdStrike integration is set up, it can take up to 10 minutes for the initial sync to take place. During this time, devices may be missing the correct CrowdStrike verification state and the Device Settings page will show that “Waiting to sync”. After this time, devices will correctly show the state on their device details page and the Device Integration page will show the most recent sync time.
In the case of a recoverable error (e.g. the CrowdStrike API is unresponsive), the CrowdStrike integration may show that it has failed to sync. If so, the Device Settings page will show the time of last successful sync as well as the most recent failure to sync. When we are able to reach the CrowdStrike API, the errors will be resolved automatically.
In the case of a unrecoverable error (e.g. the API client is deleted or the permissions have been altered), the CrowdStrike integration will stop attempting to connect. Admins will be notified via email that the CrowdStrike integration needs attention. For these errors, we recommend reconfiguring the integration and inputting new API client information.
Last updated 2 months ago