MongoDB Access with Twingate
Securely connect to MongoDB Atlas and self‑hosted MongoDB using Twingate
MongoDB Access with Twingate
MongoDB can be deployed as a fully managed MongoDB Atlas cluster or as a self‑hosted instance. Twingate allows you to route traffic securely to either deployment while enforcing network access controls.
- MongoDB Atlas: Securing Databases
- MongoDB Atlas: Securing Admins
- Self-hosted MongoDB: Securing Databases
Prerequisites
- Remote Network & Connector – Create a Remote Network in Twingate and deploy one or more Connectors:
- Place Connectors inside the same network as the database (for self-hosted) or in a secure egress location (for Atlas).
- Use the private IP address of Connectors for firewall rules whenever possible.
- Use the public IP address only when required by the service (e.g. Atlas IP Access List).
- MongoDB cluster or instance – Either a MongoDB Atlas project and cluster, or a self‑hosted MongoDB server.
Tip: Use PrivateLink for Private Connectivity
If you are deploying in AWS, Azure, or GCP, MongoDB Atlas supports PrivateLink (AWS/Azure) and Private Service Connect (GCP) for fully private connections.
With these features enabled:
- Your Connector connects to a private endpoint inside your VPC/VNet.
- All traffic stays on the cloud provider’s internal network fabric — never traversing the public internet.
- No need to allowlist Connector public IP addresses in the Atlas IP Access List — access is automatically restricted to your private network.
See MongoDB’s docs on Private Endpoint Connections for setup steps.
MongoDB Atlas: Securing Databases
MongoDB Atlas restricts incoming connections to IP addresses defined in its IP Access List.
Step 1 – Create a Twingate Resource
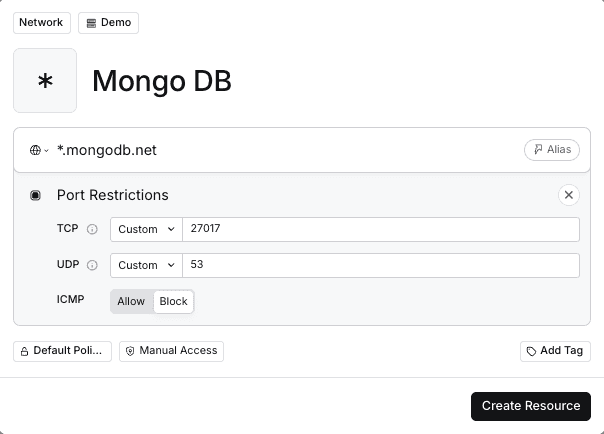
- In the Twingate Admin Console, create a Resource for your MongoDB Atlas cluster host (e.g.
*.mongodb.net). Atlas uses TLS on TCP port27017by default for direct connections and will need to handle DNS requests over UDP port53. See MongoDB’s reference to default ports. - Note the public IP addresses of your Connector(s).
Step 2 – Add Connector IP Addresses to the IP Access List
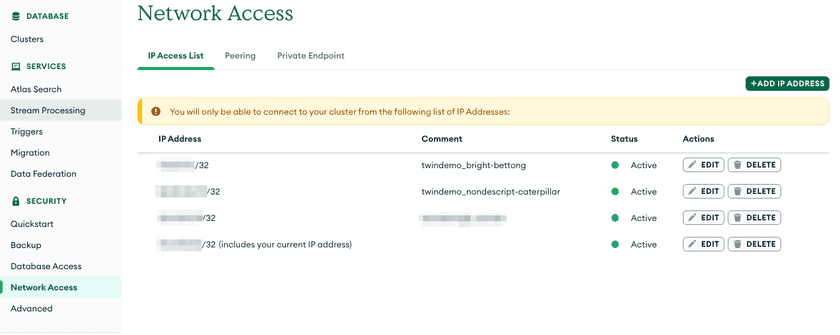
- Log in to the MongoDB Atlas console and open Network Access.
- Click Add IP Address and enter the public IP address of your Connector. Repeat for each Connector. This adds the address to the IP Access List and allows Atlas to accept connections from it.
- Save the changes. Connections from other IP addresses will be blocked.
Step 3 – Connect to your database
Use mongosh or another MongoDB client with the Twingate Client running. Example:
mongosh "mongodb+srv://cluster0.abc123.mongodb.net/mydatabase" --username <username> --password <password>For direct (mongodb://) URIs, include --port 27017.
MongoDB Atlas: Securing Admin Access
Restricting access to the Atlas Admin Console (cloud.mongodb.com) is as important as securing the databases themselves. By default, the console is accessible from any IP address. MongoDB can enable IP Access Lists for the Atlas UI at the organization level, these are separate from database project IP allow lists.
Step 1 – Request IP Access Lists for the Atlas UI
- In the MongoDB Atlas console, go to Organization → Settings.
- If you don’t see IP Access List for the Atlas UI, contact MongoDB Support to enable it.
Step 2 – Create a Twingate Resource for the Atlas UI
-
In the Twingate Admin Console, create a Resource for:
cloud.mongodb.comPort:
443(HTTPS) -
Use the same Remote Network that contains your database-access Connectors.
-
Note the public IP address(es) of those Connectors (Admin Console → Remote Network → Connectors → Public IP).
Step 3 – Add Connector IP Addresses to the Atlas UI IP Access List
- In Organization → Settings → IP Access List, add each Connector public IP address.
- Save changes — only these IP addresses will be able to load the Atlas UI.
Step 4 – Verify Access via Twingate
- Run the Twingate Client and connect.
- Access https://cloud.mongodb.com. The UI should load only when traffic originates from the authorized Connector IP addresses.
Tip: You can also secure behind SSO
If your organization uses SSO, you can also enforce access via SaaS App Gating for additional identity-based control.
Self‑hosted MongoDB: Securing Databases
For on‑premises or self‑hosted MongoDB instances, you control the server and network:
- Create a Twingate Resource with the host set to your MongoDB server’s IP address or DNS name and port
27017. - Restrict inbound traffic on the server’s firewall to only allow connections from the Connector’s private IP address. Alternatively, configure
net.bindIpin yourmongod.confto listen only on interfaces accessible via Twingate. Use the public IP only when the Connector must reach the server via the internet. - Connect using
mongoshthrough Twingate.
Troubleshooting Database Connections
If you’re having trouble connecting to your database via Twingate, check the following common issues.
Connection String Type Matters (mongodb:// vs mongodb+srv://)
MongoDB supports two connection string formats. Each format has different network requirements:
-
mongodb+srv://- Uses DNS SRV records to discover cluster nodes (common with Atlas)
- Requires DNS resolution in addition to TCP
27017 - Twingate Resources must allow the cluster hostname and DNS access (port
53)
-
mongodb://- Connects directly to specific hosts and ports
- Each hostname or IP address in the URL must be reachable from the Connector
Important
Ensure your Twingate Resource definitions match the connection string type you are using.
Mismatches between DNS-based (mongodb+srv://) and direct (mongodb://) connections are a common cause of failed connections.
For more details, see MongoDB’s connection string documentation:
Common Errors and Checks
- Connection refused: Ensure Connector IP addresses are in the Atlas IP Access List, or verify firewall and
bindIpsettings for self-hosted MongoDB. - Authentication error: Verify credentials and database name. Atlas requires TLS.
- Timeouts or slow connections: Confirm Connectors are online, reachable, and not blocked by firewall or security group rules.
Using Twingate Recent Activity
In the Twingate Admin Console, check Recent Activity for the Resource:
- DNS Failed: The Connector could not resolve the hostname (DNS access or routing issue).
- Connection Failed: The Connector resolved DNS but could not reach the database (routing, firewall, or IP allow list issue).
- No Activity: The Client did not send traffic (Client not running, Resource missing, or another VPN interfering).
For more troubleshooting guidance, see the Twingate Troubleshooting Guide.
Related Resources
Last updated 2 months ago