How Windows Start Before Logon Works
Background
Windows Start Before Logon (SBL) is a Windows-specific workflow where the device is able to connect to a remote network at the Windows logon prompt, before the user has authenticated themselves on their machine. This is normally achieved using a traditional VPN network connection, usually to access a domain controller for authentication and/or group policy application.
Twingate supports the SBL workflow using the following combination of supported functionality:
- Device-only Resource Policies
- Twingate Windows Client [v1.0.14 or later]
- (Recommended) Trusted Devices
If you are looking to use SBL with your Active Director Domain Controller, we also recommend reviewing our use case on Active Directory with Twingate.
Example Configuration: Domain Controller access via SBL
After completing the following steps, you will have the following configuration:
- Users will need to sign in to Twingate at least once every 30 days.
- Your domain controllers will be accessible to users that must be on Windows devices that are also marked as trusted in Twingate.
- Domain controllers will be accessible at the Windows logon prompt as long as users have signed into Twingate within the last 30 days.
- Add your Domain Controller addresses as Resources in Twingate. Follow the instructions available in our Active Directory with Twingate example.
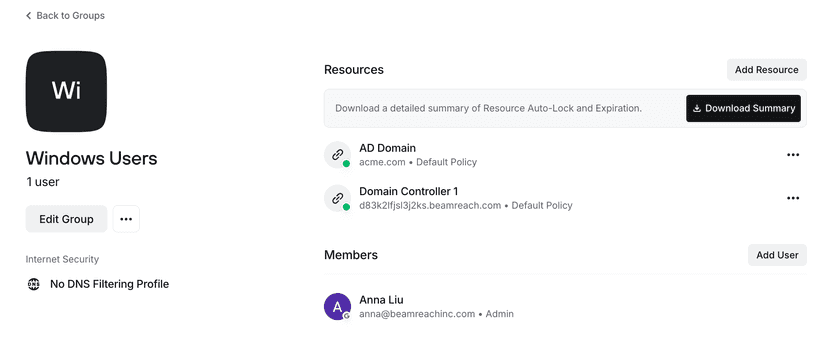
- Create a Group and add the Domain Controller Resources to the group. You should also add Users you wish to access these Resources to the Group. An example is shown in the screenshot below.
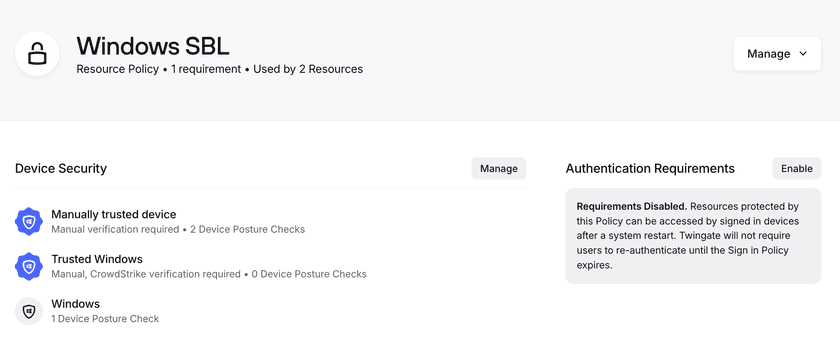
- Create a new Resource Policy called “Windows SBL”. Select “Create Resource Policy” from the “Policies” tab in the Admin console.
- Disable user authentication requirements for the Windows SBL Policy, and enable device requirements. In the example below we have restricted access to Windows devices only, allowing both trusted and untrusted devices to be authorized for access.
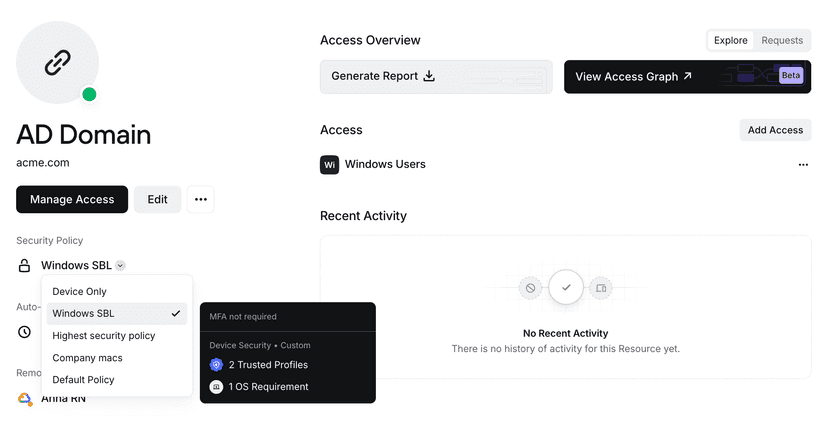
- Modify the Resource Policy for each Resource. This enables the device-only policy specifically for the Resources and Users that are in this Group.
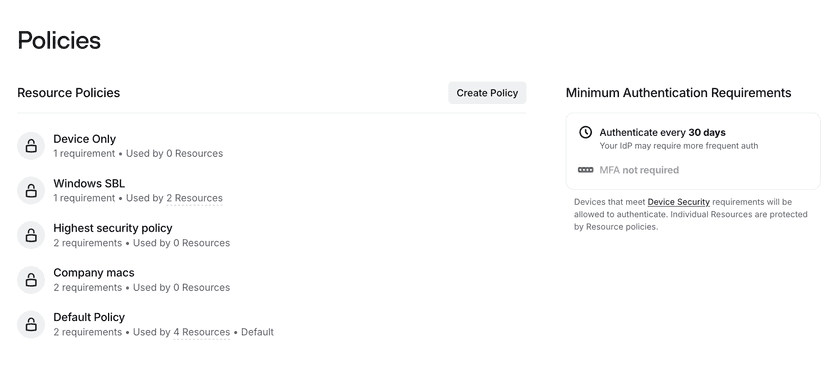
- Verify the Minimum Authentication Requirements session length matches your requirements. Minimum Authentication Requirements are applied when users sign in to the Twingate Client application. Unless the configuration is modified, the session length defaults to 30 days, which means that users must re-authenticate at least once every 30 days for the Client to remain signed in. This session length persists across machine restarts or re-launching the Client application unless the user logs out of the Client. Authentication for Resources then applies as follows:
- Device-only Resource Policies, such as the one we have configured here, do not have user authentication requirements, and thus are accessible as long as the Minimum Authentication Requirements session is valid and any device requirements have been met.
- Standard Resource Policies, including the Default Policy, include a user authentication requirement, which must always be re-validated between machine restarts or re-launching the Client application.
After following the above steps, the Active Directory resources you have configured will be accessible to users at the Windows logon screen under the following circumstances:
- They are using the Windows Twingate Client v1.0.14 or newer.
- They have signed in to the Twingate Client application within the last 30 days and have not logged out of the Twingate Client.
- They are using a device that has been marked as trusted in Twingate.
Last updated 1 year ago