Two-Factor Authentication
Applicability
This rule can be applied to Resource Policies, Minimum Authentication Requirements, and Admin Console Security.
Functionality
This rule controls whether the user will be prompted for two-factor authentication when attempting to access a Resource, sign in to the Network, or sign in to the Admin Console. More details on two-factor authentication can be found in our documentation.
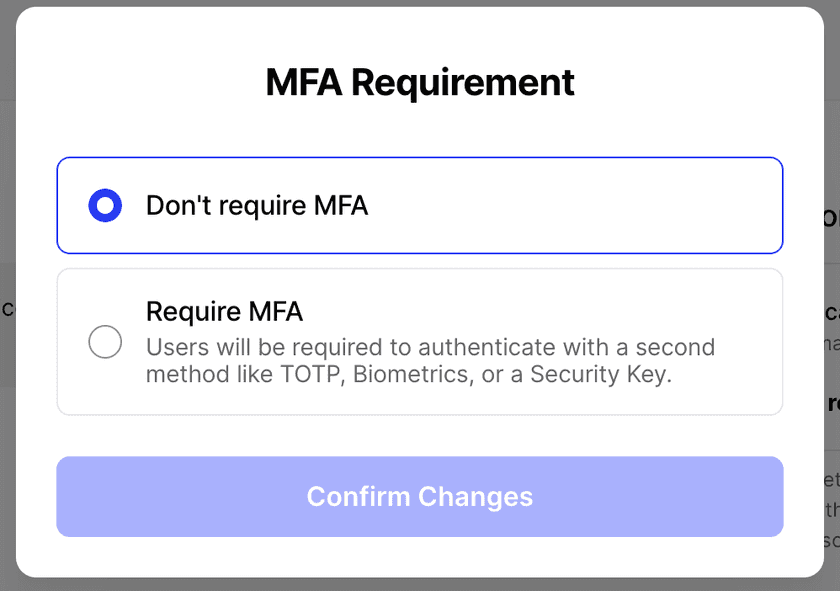
We recommend that you either set a 2FA rule on Minimum Authentication Requirements or Resource Policies, but not both, otherwise users will be asked to 2FA twice.
Configuration
When Two-Factor Authentication is required and not set up yet, you will see a notification after authenticating with your credentials.
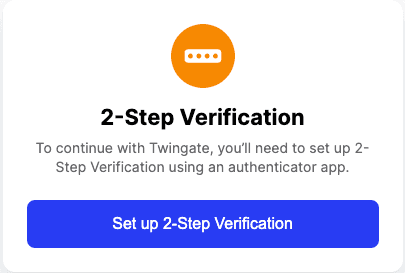
Twingate’s 2FA uses industry standard TOTP format to generate 2FA codes. You can use any TOTP-based authenticator application on Android or iOS, such as Google Authenticator (Android, iOS). Your identity provider may also include this functionality in their own mobile app.
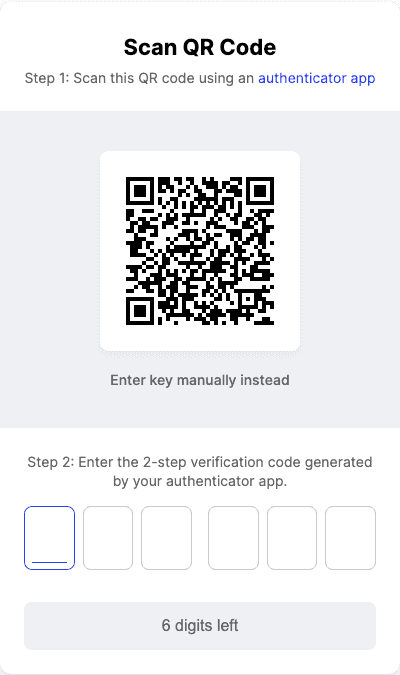
First, add a new application in your authenticator app, then scan the QR code using your phone’s camera. If you are setting 2FA up from your phone, entering the alphanumerical ID instead may be easier. After you’ve set it up on your phone, confirm that everything is working correctly by entering the code that’s generated in the app.
Going forward, you will need to enter the 2FA code from the app you set it up on every time you access a Resource or network protected by 2FA.
After setting up TOTP for 2FA, you will be prompted to set up either a biometric method or register a security key, both of which are additional options for meeting the Twingate 2FA requirement.
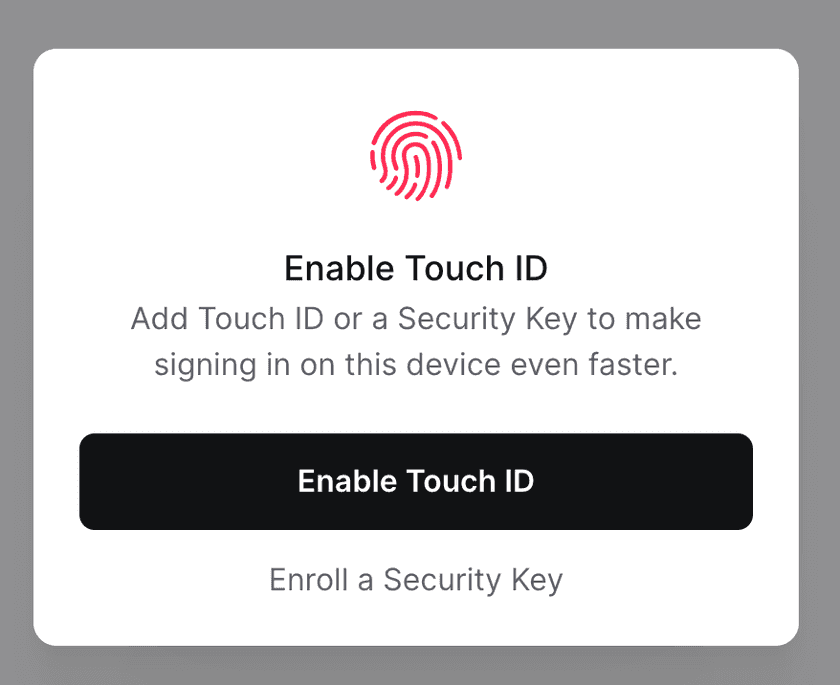
When selecting to enroll either a biometric method (e.g. Touch ID, Windows Hello) or a security key (e.g. YubiKey), you will be routed through the browser to complete registration. After registration is complete, you will be able to use these additional methods to meet the Twingate 2FA requirement.
Do not delete the authentication app or the Twingate code inside the app
If you lose access to the authentication app where Twingate 2FA is configured, you will not be able to access Twingate Resources or Networks protected by 2FA. Your Twingate Admin will need to reset your user’s 2FA and you will have to set up 2FA again.
Last updated 1 year ago