Best Practices for Designing an Internal Network with Local Peer-to-Peer Connections
In this guide, we will explore Twingate’s suggested best practices for designing an internal network to leverage local peer-to-peer (P2P) connections. By following these practices, you can optimize network performance and enhance the security of internal Resources such as servers and applications.
Understanding Peer-to-Peer Communication
Twingate’s peer-to-peer communication is a core feature of our Zero Trust Network Access (ZTNA) service, enabling direct, secure connections between users and Resources. Unlike traditional VPN setups that route traffic through a central gateway, Twingate’s peer-to-peer technology allows users to communicate more directly with Connectors in Remote Networks. This reduces latency, improves connection speeds, and enhances overall performance by minimizing unnecessary hops.
Local Peer-to-Peer: What It Is and Why It’s Important
Local peer-to-peer refers to direct communication between users and Resources within the same local network. Twingate’s implementation of local peer-to-peer offers several advantages:
- Security Enhancements: Twingate’s Zero Trust approach ensures that only authenticated and authorized users can initiate peer-to-peer connections, maintaining strict control over Resource access.
- Efficient Resource Access: Users can directly access Resources on the same network, improving response times and productivity.
- Bandwidth Optimization: By keeping data exchanges within the local network, external bandwidth usage is minimized, freeing up capacity for other operations.
Suggested Best Practices for Network Topology
Network Design Overview
A robust network design is crucial for maximizing the benefits of Twingate’s local peer-to-peer connections. Here is a recommended topology:
-
Single Physical Network with Two VLANs
- VLAN 1: Hosts all Resources, including servers, systems, and two Twingate Connectors.
- VLAN 2: Dedicated to users, DHCP, and other end user devices.
-
Strict Traffic Segregation
- No traffic is allowed between VLAN 1 and VLAN 2 except for the private IP addresses of the Twingate Connectors.
- This segregation ensures that users cannot directly access Resources on VLAN 1 without proper authentication and authorization through Twingate.
Implementation Details
-
Connector Placement
- Place two Twingate Connectors in VLAN 1 to handle incoming user requests from VLAN 2.
-
Traffic Routing
- Users in VLAN 2 will route traffic through the Twingate Connectors to access Resources in VLAN 1.
- This setup ensures that all user access is mediated by Twingate’s security protocols, leveraging local peer-to-peer connections for efficiency.
-
Firewall Configuration
- Implement firewall rules that only allow traffic from VLAN 2 to the Connectors’ private IP addresses in VLAN 1.
- Block all other inter-VLAN traffic to maintain strict control over Resource access and protect sensitive data on VLAN 1.
Example Network Configuration
Here’s an example network, illustrating the recommended topology for local peer-to-peer connections with Twingate:
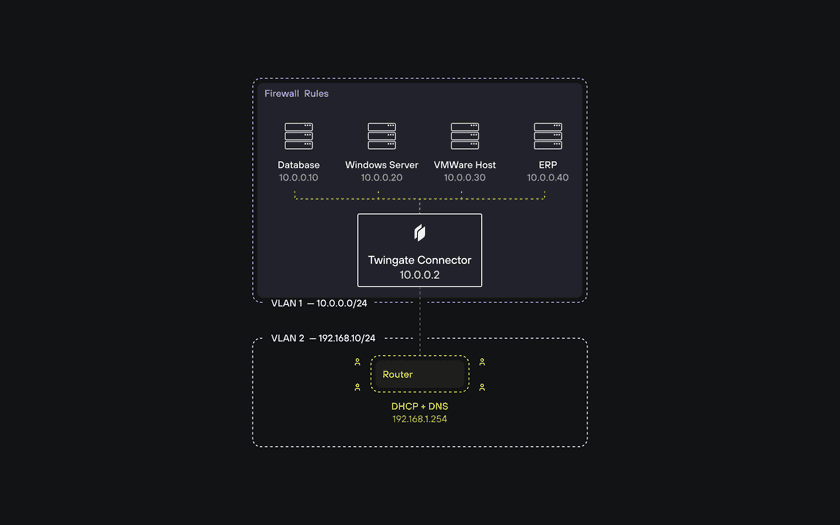
Firewall Rules
Source | Destination | IP/Port | Action--------------------------------------VLAN 2 | VLAN 1 | 10.0.0.2:* | AllowVLAN 2 | VLAN 1 | *:* | BlockVLAN 1 | VLAN 2 | *:* | BlockVLAN Configuration Details
- VLAN 1 (Resources):
- Hosts servers, systems, and Twingate Connectors.
- Connectors are responsible for mediating user requests from VLAN 2 to access Resources.
- VLAN 2 (Users):
- Dedicated to end user devices, and DHCP and DNS services.
- Users access Resources in VLAN 1 through Twingate Connectors.
As the firewall rules are applied in order from top to bottom, traffic from VLAN 2 (users) will only be allowed through to the IP address for the one Connector, on any port, but denied for all other attempts to access systems in VLAN 1. All traffic from VLAN 1 will be allowed to access VLAN 2.
Implementing Firewall Rules for VLAN Segregation
Firewall rules play a critical role in maintaining the security and integrity of the network. Here is a general overview of the necessary firewall rules:
- Allow VLAN 2 to Connector IP addresses on VLAN 1:
allow traffic from VLAN 2 to Connector_IPs on VLAN 1 on required ports
- Block All Other Inter-VLAN Traffic:
block all other traffic between VLAN 1 and VLAN 2
Implementing Firewall Rules for VLAN Segregation
This section provides examples of configuring firewall rules to allow traffic between VLANs only through Twingate Connectors on four commonly used commercial on-premises firewalls: Palo Alto Networks NGFW, Fortigate, Sophos XG, and Barracuda CloudGen Firewall.
1. Palo Alto Networks NGFW
To segregate VLANs and ensure that traffic between VLAN 1 (Resources) and VLAN 2 (Users) only passes through Twingate Connectors, you start by creating and defining VLANs for your Resources and users. This involves setting up the VLANs within the network configuration and assigning the necessary interfaces. Next, you establish security zones corresponding to each VLAN, ensuring that these zones are correctly mapped within the firewall’s configuration.
Following this, you define security policies that specify the traffic allowed between VLANs. In this case, you would create a policy that permits traffic from the user VLAN to specific IP addresses in the resource VLAN, which would represent the Connector(s). This includes setting the source and destination zones and defining the allowed services and IP addresses. Additionally, you may need to implement policy-based forwarding (PBF) rules to direct traffic according to your security policies, ensuring that it is routed correctly through the firewall.
Utilizing Strata Cloud Manager’s best practice recommendations can help in aligning your configuration with security standards, identifying policy anomalies, and maintaining robust security controls. Regular monitoring and adjustments based on the insights provided by Strata Cloud Manager will ensure that your policies are effective and your network is secure. For more detailed steps and best practices, you can refer to the Strata Cloud Manager documentation and the official Palo Alto Networks resource center.
2. Fortinet FortiGate
To configure FortiGate for VLAN segregation with Twingate Connectors you would follow several steps involving VLAN configuration and firewall policies.
First, you need to configure the VLANs on the FortiGate device. This involves creating the VLANs and assigning them to the appropriate interfaces. You can do this through the FortiGate GUI by navigating to the Network section, selecting VLAN, and then adding new VLANs with the necessary identifiers (VIDs) and interface assignments.
Next, you need to set up firewall policies to control the traffic between the VLANs. In the FortiGate GUI, go to the Policy & Objects section and create a new policy. Define the source VLAN and the destination IP addresses that are allowed to communicate. Ensure that you specify the exact IP addresses or subnet in the destination field to limit access to only those addresses. Configure the action to allow traffic and apply the necessary security profiles if required.
To enhance security and enforce the policy, use FortiGate’s capabilities to apply strict firewall rules that prevent any other traffic between the VLANs. This ensures that only the defined traffic is permitted, maintaining isolation and security for the Resources in the destination VLAN.
For more detailed steps and configuration options, you can refer to the Fortinet Getting Started with FortiGate guide and Configuring VLANs.
3. Sophos XG
To configure a Sophos XG Firewall to allow devices in one VLAN to communicate with only the Connector in another VLAN, you need to follow several key steps. First, create VLAN interfaces for both VLANs involved. This is done by navigating to Network > Interfaces and selecting Add interface, then Add VLAN. You’ll need to specify the appropriate settings such as VLAN ID, IP address, and assign them to the correct zones.
After setting up the VLANs, create firewall rules to control the traffic between them. Go to Rules and Policies and define the necessary policies. In this case, you will create rules that permit traffic from VLAN 2 to the Connector(s) IP addresses in VLAN 1. Ensure that these rules are restrictive enough to block any other traffic to or from the destination VLAN, except through the specified IP addresses.
For detailed guidance and step-by-step instructions, refer to this Sophos XG documentation.
4. Barracuda CloudGen Firewall
To configure a Barracuda CloudGen Firewall to allow devices in one VLAN to communicate with only the Connector in another VLAN, you can follow a high-level process involving VLAN configuration, creating access rules, and applying the necessary network security policies.
First, you’ll need to configure the VLANs on the Barracuda CloudGen Firewall. This involves setting up the VLAN interfaces and assigning them to the appropriate physical or virtual ports. Next, you’ll need to create the access rules. These rules specify which IP addresses in the source VLAN are allowed to communicate with which specific IP addresses in the destination VLAN. You can do this using the Firewall Admin interface, where you navigate to the “Configuration” tab and define the necessary rules under the “Firewall” section.
In these rules, ensure that you set the source and destination network objects correctly, specifying the entire range for VLAN 2 (users) as the source and only the Connector IP address in VLAN 1 as the destination. To block all other traffic to the destination VLAN, you would create a default deny rule that applies to any traffic not explicitly permitted by your earlier rules.
Finally, you will apply these configurations and test to ensure that the devices in the source VLAN can only communicate with the specified IP addresses of the Connector(s) in the destination VLAN, with all other traffic being blocked.
For more detailed steps, you can refer to the official Barracuda documentation at Barracuda CloudGen Firewall Overview, Getting Started with Barracuda CloudGen Firewall, and Firewall Admin Configuration.
Conclusion
Implementing Twingate with a local peer-to-peer network architecture offers significant benefits in terms of performance and security. By following the recommended network topology and firewall configurations outlined in this guide, you can ensure efficient, secure access to internal Resources.
For more detailed information on how Twingate works, peer-to-peer communication, and troubleshooting, please refer to the following resources:
Last updated 1 year ago