Device Security Guide
Twingate enables you to define what it means for a device to be trusted and then incorporate these definitions into Security Policies for your Network or for individual Resources.
Device Security
Twingate supports two categories of device requirements, both of which can be incorporated into authenticating into the Client as well as accessing a Resource.
- Minimum OS Requirements: These requirements identify the minimum device requirements to access Twingate. These checks, using native device posture details from the Twingate desktop and mobile applications, can require checks such as hard drive encryption and screen lock passwords to be enabled.
- Trusted Profiles: These requirements can be configured for policies requiring additional security. In addition to the native device posture checks, admins can also require a Trust Method. The Trust Method identifies devices that meet a more stringent device verification method.
These requirements are applied at the sign-in level and can also be associated with specific Resource Policies so that only specific devices can be used to access individual Resources.
A good analogy is wristbands: a device can have multiple or no wristbands, depending on if it meets the requirements of either any Trusted Profiles or minimum OS requirement. For example, if a device meets a Trusted Profile and also the macOS minimum requirements, it will have wristbands for both. When it comes to signing in to Twingate, any device with any wristband can sign in. When it comes to accessing a Resource, only devices with the allowed wristbands via the assigned Resource Policy will have access.
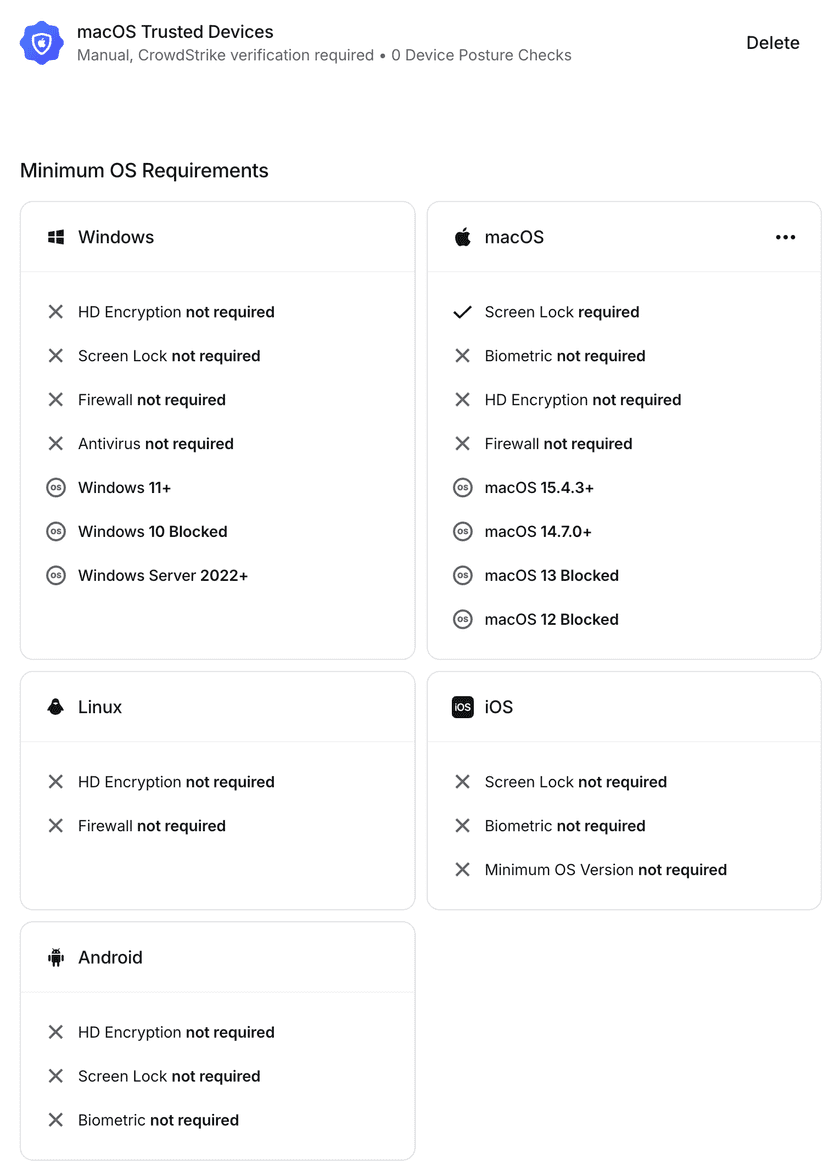
Common configurations
The following are examples of how you can configure Device Security and Security Profiles.
| Scenario | Device Security configuration | Security Policies configuration |
|---|---|---|
| Only allow macOS and iOS, both with basic posture checks | - Use Minimum OS Requirements to block OS access for Android, Windows, and Linux - Configure posture checks in Minimum OS Requirements for macOS and iOS | - Create a policy that allows All Devices or a custom setting to just allow the macOS and iOS Minimum OS Requirements profiles |
| Employees’ devices are marked as trusted; contractors are not | - Configure Minimum OS Requirements to match the device posture checks needed for contractors’ devices - Create Trusted Profiles for the platforms used by employees, ensuring that “Manual Trust” is selected as the Trust Method | - Associate Trusted Profiles with the Resources that employees access - Associate Minimum OS Requirements with the Resources that contractors access |
| Blocks all Android devices except for test devices | - Use Minimum OS Requirements to block OS access for Android - Create a Trusted Profile for Android, ensuring that “Manual Trust” is selected as the Trust Method and that all test devices are marked as Trusted | - Add Android Trusted Profile as an allowed device |
| Only allow macOS devices with MDM/EDR integration to authenticate | - Block the macOS platform in Minimum OS Requirements - Set up the applicable MDM/EDR integration - Create a Trusted Profile for macOS, ensuring that the company-supported MDM/EDR integration is required | - Add the macOS Trusted Profile to any Policies on Resources that macOS devices should access |
Configuring Device Security
By default, all platforms are allowed with no native device posture checks.
If specific platforms should not be used to access Twingate, the Minimum OS Requirement for that platform can be set to block the particular OS. If specific platforms should have custom native device posture checks, those can be enabled for each Minimum OS Requirement.
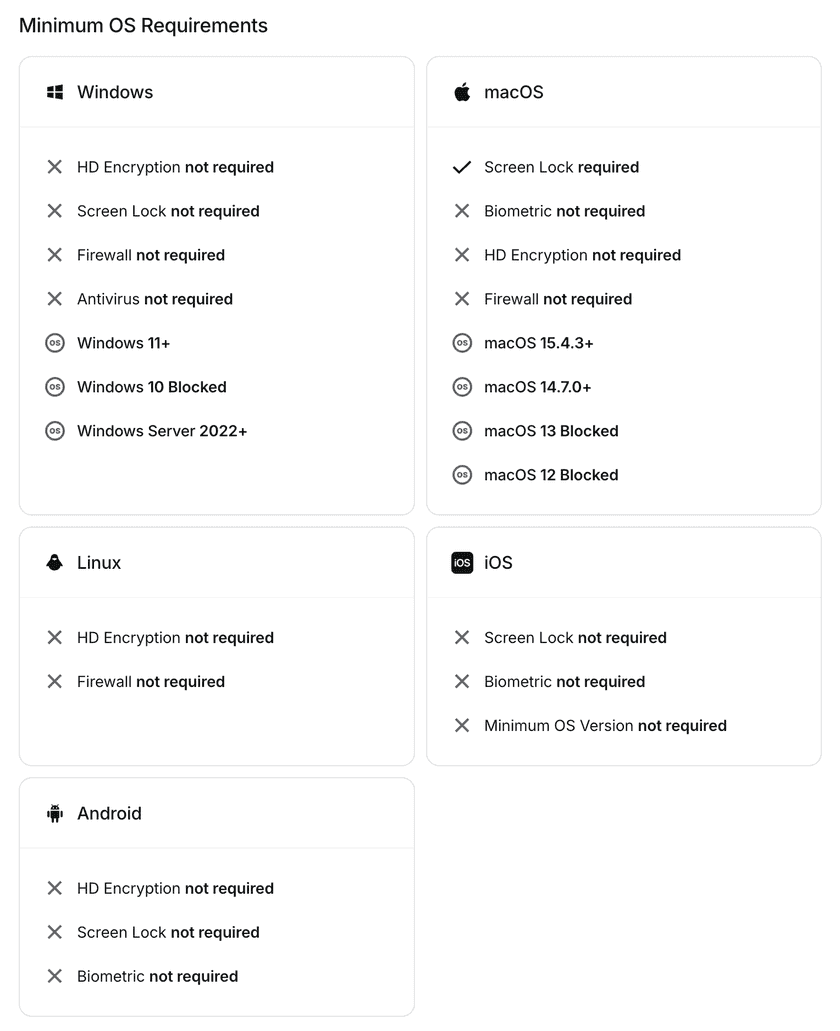
| Platform | Device posture check |
|---|---|
| Windows | - HD Encryption - Screen Lock - Firewall - Antivirus - Minimum OS Version |
| macOS | - Screen Lock - Biometric Configuration - Firewall (only available in the macOS standalone app) - HD Encryption (only available in the macOS standalone app) - Minimum OS Version |
| Linux | - HD Encryption - Firewall |
| iOS | - Screen Lock - Biometric Configuration - Minimum OS Version |
| Android | - HD Encryption - Screen Lock - Biometric Configuration |
For more information on how device posture checks are collected, see here.
If your organization has specific devices that are considered trusted, you can create a Trusted Profile for those platforms. Within a Trusted Profile, you can set which verification methods are required and also set additional device posture requirements. The Trusted Profiles can then be incorporated into either the sign-in policy or Resource Policies to gate access. The currently supported verification methods are:
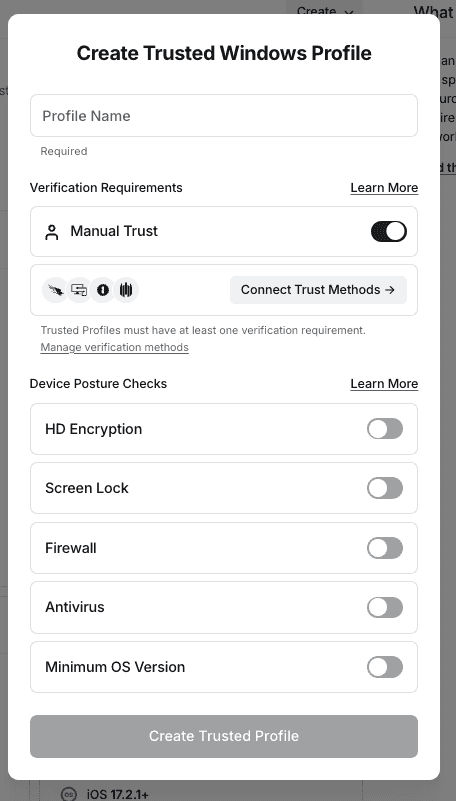
Configuring Policies
For sign-in, any device that meets any of the Minimum OS Requirements or Trusted Profiles can be used to access Twingate. Note that the minimum authentication requirements will also need to be met.

To enforce requirements on the devices that can be used to access a specific Resource, you can identify which groups of requirements are needed to satisfy that Resource Policy.
- Any Device: Any device that meets Device Security requirements will be allowed, including devices that meet either Minimum OS Requirements or Trusted Profiles.
- Only Trusted Devices: Only devices that meet Trusted Profile requirements will be allowed.
- Custom: Only devices that meet the specified set of requirements will be allowed.
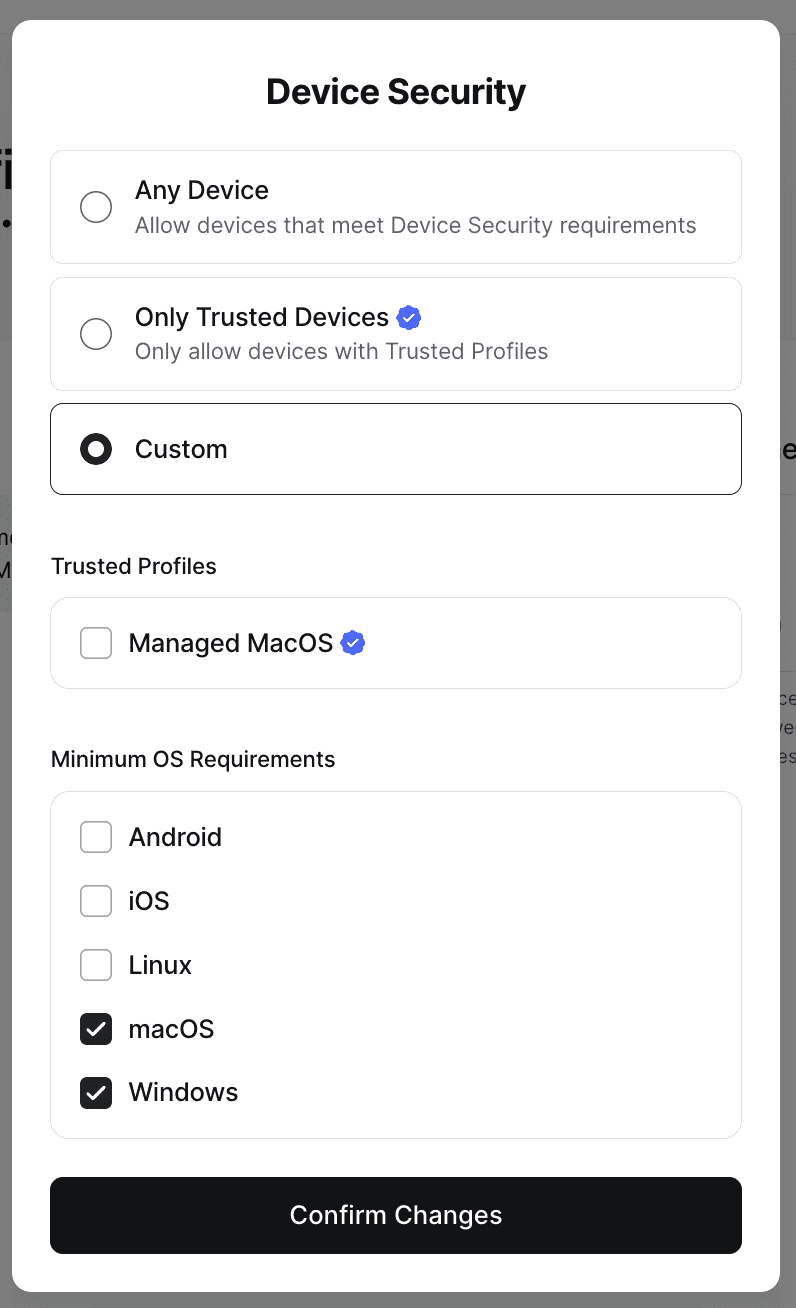
See the article on Security Policies for more information.
If a device doesn’t meet the Device Security requirements, it will be blocked from logging into Twingate or accessing protected Resources.
Last updated 3 months ago