Solving the usability problem to unlock Zero Trust adoption
Tony Huie
•
Apr 14, 2022
Security has a usability problem.
When given a choice between security and convenience, people almost always choose the latter. As a result, security products that add too much friction, complexity, and frustration end up ineffective. This observation might sound obvious, but user-centric design is a rarity in the security space.
When we started Twingate a few years ago, we noticed that nowhere does security have a bigger usability problem than access control. On the surface, access appears to be a simple problem. But look at any company and you’ll see that access control is a complex orchestration of passwords, VPNs, NACs, etc. that is suboptimal for everyone involved.
So with usability as a focus, we set off to tackle this problem by focusing initially on designing a network access product that could be a simple yet powerful alternative to VPNs.
As it turns out, people really do care about good design. Since our launch 18 months ago, we’ve been humbled by the reception we’ve received from organizations and users all over the world.
Today, we’re excited to share that we’ve raised $42 million in Series B funding led by BOND, with significant participation from our existing investors WndrCo, 8VC, and SignalFire. We’re excited to welcome Jay Simons from BOND to a seasoned investor group that has built and backed some of the most successful software companies in the world. Jay joined Atlassian when it was the size of Twingate today, and built a pioneering product-driven model that enabled Atlassian to become one of the most widely used software platforms in the world. We couldn’t imagine a better partner to guide us as we build Twingate.
With this new round of funding, we’ll be investing aggressively to scale our team to meet the demands of our rapidly growing global customer base. In addition, we’re excited to announce two new programs:
The Twingate Partner Alliance, which will enable us to work even more closely with MSPs, resellers, and ISVs. We already work with many partners around the world, and we’re excited to invest even more heavily in our partner community.
The Twingate Starter Plan, a new, fully-free tier for any individual or organization to get started with Twingate, regardless of budget. Whether you’re a startup, hobbyist, or a Fortune 500 company, we want to make Twingate the most accessible platform for securing access to your private resources.
We’re just getting started and also wanted to take the opportunity to share what we’re building towards in the coming years.
Access Control is the Cybersecurity Imperative of the Next Decade
If you talk to buyers, vendors, and analysts in the IT and security industry, you’ll find no shortage of products for today’s security challenges. That in itself poses a challenge for companies. With security breaches growing in frequency and severity, security and IT teams are forced to string together an alphabet soup of complex tools that aren’t designed to work well together.
As a result, users often end up with the burden of making the difficult choice between security and convenience (and are then chastised when they inevitably opt for convenience).
At the root of this problem is a brittle access control model that was designed in the 1990s and has not evolved to meet the demands of modern work. Even for their most important resources, companies typically manage access through some combination of:
Static usernames and passwords;
Private, protected networks tied to physical locations (aka offices); and
Strictly managed devices (often coupled with VPN access for remote access into those networks).
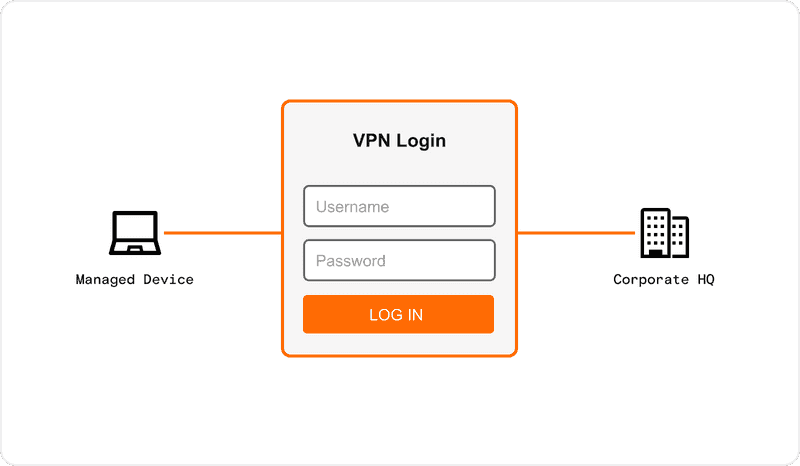
VPN Traditional Remote Access Model
However, all of today’s user behaviors illustrate the shortcomings of this model:
Two-thirds of users admit to reusing passwords (and that’s just those who admit it!), which results in password compromises being one of the most common ways companies are breached.
Users can no longer be assumed to work from protected, company-controlled networks. People now work from everywhere, accessing corporate resources through all types of networks (home, coffee shops, airports, etc).
People use multiple devices for work (including BYOD/personal devices) and access cloud-based/SaaS services that can be accessed from anywhere, without a VPN.
Moreover, the tools and practices used to enforce this model create friction and frustration for users. Clunky VPNs slow down network traffic, frequent password resets drive users crazy, manual IP address allow-listing is brittle and cumbersome, and device management products are too invasive for personal devices.
The unfortunate result is that users actively look to circumvent these security measures, IT & security teams are overstretched trying to mitigate these resulting behaviors, and ultimately companies aren’t protected.
At Twingate, we believe there’s a better way. There is a superior access control model that solves these challenges, and we see every company shifting to this model over the next decade: Zero Trust.
The Usability Problem Holding Back Zero Trust
If you speak to enough security and IT leaders about how to solve today’s security challenges, the conversation will invariably turn to Zero Trust. Popularized by companies like Google, this security framework has its roots in the earliest days of the internet and has been heralded by analysts for over a decade. Even the U.S. federal government has made Zero Trust an imperative across all its departments and agencies. So, you may wonder, given this history, why hasn’t Zero Trust been adopted more widely?
The challenge is that while Zero Trust has emerged as the consensus security model of the future, IT and security leaders will tell you it is extremely challenging to put into practice. It requires too much change management, too much manual orchestration of disparate tools, too many resources, and too much patience (given what’s expected to be a multi-year process).
Our mission at Twingate is to change that dynamic by dramatically simplifying the journey towards Zero Trust.
Another challenge is that Zero Trust is frequently misused in today’s noisy security market. So, let’s start with a clear definition of what Zero Trust means to us.
At its core, Zero Trust is about answering one very simple question for every access attempt:
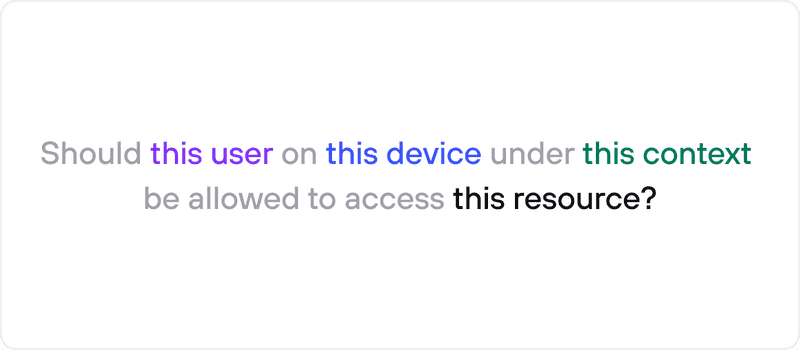
Zero Trust Access Framework
However, this question is deceptively simple, because when you play it out in any typical organization, it becomes very complex, very fast. Is the user a full time employee, a contractor, or an automated service? Is the device a company device, personal device, or a server? Can you tell if a user and device pair is working in an office, at home, or in a public cloud environment? Do we allow access via SSO, MFA, or VPN?
And even when you have all of this information, how do you determine whether access should be granted immediately, routed for approval, or denied? How long should access be allowed? The permutations get unwieldy very quickly.
Moreover, when you need to string together 4-5 (or more) different tools to answer this question, you can begin to see how complicated this access control model can become in practice. User information is locked in an SSO or identity provider, device information is housed in a separate MDM or EDR system, and contextual information is spread out across multiple siloed products or cloistered in a SIEM.
Additionally, granting access often means orchestrating connections between those tools and network-based products like VPNs or NACs.
Unfortunately, none of these tools are designed to work together. The result is a mess of increasing complexity for admins and constant friction that gets in the way of user productivity.

Zero Trust Access Framework with Integrations
This challenge is imposing enough for larger organizations with dedicated IT teams. It is basically impossible for leanly resourced small- and medium-sized businesses.
Because of this, our belief is that poor usability is the fundamental problem preventing widespread adoption of Zero Trust.
Simplifying the On-Ramp to Zero Trust
In our view, the core capabilities required to implement Zero Trust access controls are:
Support for secure connectivity to resources across public and private networks
Device awareness for any device type, whether virtual or physical, and whether mobile, desktop, or server
Stronger multi-factor identity authentication that ideally eliminates the need for passwords
Contextual awareness of location, usage patterns, and more
Workflow automation, visibility over network activity, and a policy engine to tie this all together
Today, these capabilities are distributed across multiple systems that are often challenging to procure, integrate, and orchestrate.
So how do we get started? In our conversations with hundreds of companies, one common pain point quickly emerged: can you help us eliminate our VPN?
With that insight, we launched Twingate with a clear and immediate value proposition to start: replace your VPN with a more secure, usable, and performant solution that your workforce will love.
As a VPN replacement, we offered customers:
A dramatically simpler deployment process, with an extensive API and automation capabilities for technical teams (who often bear the brunt of wrangling with VPNs)
Powerful security controls to provide granular access permissions and mitigate the risk of broad-based network access
More flexibility by decoupling access controls from network architectures
High performance, low latency connectivity for users through a combination of smart routing, split tunneling, direct peer-to-peer connections, and leveraging well-vetted transport protocols like QUIC
A seamless, set and forget experience for end users
In addition, we built deep integrations with your existing technology stack to make it easy to get started. These integrations in turn allowed our network connectivity layer to function as a simple orchestration engine across identities, devices, and context, regardless of where that information resides.
Very quickly, we saw customers using Twingate for much more than just a VPN replacement. Customers started using Twingate to implement ephemeral access controls, enforce device restrictions on SaaS apps, extend MFA to technical infrastructure, secure automated DevOps and Infrastructure-as-Code processes, and much more.
While early conversations about Twingate started with replacing VPNs, they very quickly evolved into how we actually presented an easy on-ramp to Zero Trust.
Embraced by Innovators
We’ve been humbled by the reception of Twingate since our launch 18 months ago. Companies of all sizes, from all over the world, have retired legacy network technologies like VPNs and NACs and started their Zero Trust journey with Twingate.

Today, Twingate is one of the highest-rated Zero Trust solutions on leading review sites like G2, and the winner of over 50 awards:
G2 Awards
To our customer community: we’re incredibly thankful for your tremendous support and inspiration. We’re excited to invest even more to deliver on the trust you’ve placed in us.
What’s Next
Looking ahead, our goal is to accelerate the adoption of Zero Trust by organizations around the world.
We plan to continue working to make Twingate simple enough for small businesses, yet powerful enough for the largest global enterprises, with accessible pricing plans to fit any budget (or no budget at all).
Here’s what you’ll see us investing in over the next year:
Doubling down on our distributed networking platform to provide the fastest, lowest latency connectivity experience for users in any network environment.
Extending the capabilities of our device agents to introduce device awareness and enable better access and authorization decisions based on rich, contextual device information.
Leveraging that device awareness to reimagine the authentication experience so we can reduce the reliance on passwords, improving security and reducing friction for users.
Providing extensive workflow automation, visibility, and seamless integrations with existing security solutions to unburden IT and Security teams.
If our mission is exciting to you, join us! We’re hiring across the company.
If you’re exploring Zero Trust for your company, try Twingate for free today.
If you’re a channel partner or MSP, join the Twingate Partner Alliance.
We’re excited to get to work. Let’s go!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Solving the usability problem to unlock Zero Trust adoption
Tony Huie
•
Apr 14, 2022
Security has a usability problem.
When given a choice between security and convenience, people almost always choose the latter. As a result, security products that add too much friction, complexity, and frustration end up ineffective. This observation might sound obvious, but user-centric design is a rarity in the security space.
When we started Twingate a few years ago, we noticed that nowhere does security have a bigger usability problem than access control. On the surface, access appears to be a simple problem. But look at any company and you’ll see that access control is a complex orchestration of passwords, VPNs, NACs, etc. that is suboptimal for everyone involved.
So with usability as a focus, we set off to tackle this problem by focusing initially on designing a network access product that could be a simple yet powerful alternative to VPNs.
As it turns out, people really do care about good design. Since our launch 18 months ago, we’ve been humbled by the reception we’ve received from organizations and users all over the world.
Today, we’re excited to share that we’ve raised $42 million in Series B funding led by BOND, with significant participation from our existing investors WndrCo, 8VC, and SignalFire. We’re excited to welcome Jay Simons from BOND to a seasoned investor group that has built and backed some of the most successful software companies in the world. Jay joined Atlassian when it was the size of Twingate today, and built a pioneering product-driven model that enabled Atlassian to become one of the most widely used software platforms in the world. We couldn’t imagine a better partner to guide us as we build Twingate.
With this new round of funding, we’ll be investing aggressively to scale our team to meet the demands of our rapidly growing global customer base. In addition, we’re excited to announce two new programs:
The Twingate Partner Alliance, which will enable us to work even more closely with MSPs, resellers, and ISVs. We already work with many partners around the world, and we’re excited to invest even more heavily in our partner community.
The Twingate Starter Plan, a new, fully-free tier for any individual or organization to get started with Twingate, regardless of budget. Whether you’re a startup, hobbyist, or a Fortune 500 company, we want to make Twingate the most accessible platform for securing access to your private resources.
We’re just getting started and also wanted to take the opportunity to share what we’re building towards in the coming years.
Access Control is the Cybersecurity Imperative of the Next Decade
If you talk to buyers, vendors, and analysts in the IT and security industry, you’ll find no shortage of products for today’s security challenges. That in itself poses a challenge for companies. With security breaches growing in frequency and severity, security and IT teams are forced to string together an alphabet soup of complex tools that aren’t designed to work well together.
As a result, users often end up with the burden of making the difficult choice between security and convenience (and are then chastised when they inevitably opt for convenience).
At the root of this problem is a brittle access control model that was designed in the 1990s and has not evolved to meet the demands of modern work. Even for their most important resources, companies typically manage access through some combination of:
Static usernames and passwords;
Private, protected networks tied to physical locations (aka offices); and
Strictly managed devices (often coupled with VPN access for remote access into those networks).

VPN Traditional Remote Access Model
However, all of today’s user behaviors illustrate the shortcomings of this model:
Two-thirds of users admit to reusing passwords (and that’s just those who admit it!), which results in password compromises being one of the most common ways companies are breached.
Users can no longer be assumed to work from protected, company-controlled networks. People now work from everywhere, accessing corporate resources through all types of networks (home, coffee shops, airports, etc).
People use multiple devices for work (including BYOD/personal devices) and access cloud-based/SaaS services that can be accessed from anywhere, without a VPN.
Moreover, the tools and practices used to enforce this model create friction and frustration for users. Clunky VPNs slow down network traffic, frequent password resets drive users crazy, manual IP address allow-listing is brittle and cumbersome, and device management products are too invasive for personal devices.
The unfortunate result is that users actively look to circumvent these security measures, IT & security teams are overstretched trying to mitigate these resulting behaviors, and ultimately companies aren’t protected.
At Twingate, we believe there’s a better way. There is a superior access control model that solves these challenges, and we see every company shifting to this model over the next decade: Zero Trust.
The Usability Problem Holding Back Zero Trust
If you speak to enough security and IT leaders about how to solve today’s security challenges, the conversation will invariably turn to Zero Trust. Popularized by companies like Google, this security framework has its roots in the earliest days of the internet and has been heralded by analysts for over a decade. Even the U.S. federal government has made Zero Trust an imperative across all its departments and agencies. So, you may wonder, given this history, why hasn’t Zero Trust been adopted more widely?
The challenge is that while Zero Trust has emerged as the consensus security model of the future, IT and security leaders will tell you it is extremely challenging to put into practice. It requires too much change management, too much manual orchestration of disparate tools, too many resources, and too much patience (given what’s expected to be a multi-year process).
Our mission at Twingate is to change that dynamic by dramatically simplifying the journey towards Zero Trust.
Another challenge is that Zero Trust is frequently misused in today’s noisy security market. So, let’s start with a clear definition of what Zero Trust means to us.
At its core, Zero Trust is about answering one very simple question for every access attempt:

Zero Trust Access Framework
However, this question is deceptively simple, because when you play it out in any typical organization, it becomes very complex, very fast. Is the user a full time employee, a contractor, or an automated service? Is the device a company device, personal device, or a server? Can you tell if a user and device pair is working in an office, at home, or in a public cloud environment? Do we allow access via SSO, MFA, or VPN?
And even when you have all of this information, how do you determine whether access should be granted immediately, routed for approval, or denied? How long should access be allowed? The permutations get unwieldy very quickly.
Moreover, when you need to string together 4-5 (or more) different tools to answer this question, you can begin to see how complicated this access control model can become in practice. User information is locked in an SSO or identity provider, device information is housed in a separate MDM or EDR system, and contextual information is spread out across multiple siloed products or cloistered in a SIEM.
Additionally, granting access often means orchestrating connections between those tools and network-based products like VPNs or NACs.
Unfortunately, none of these tools are designed to work together. The result is a mess of increasing complexity for admins and constant friction that gets in the way of user productivity.

Zero Trust Access Framework with Integrations
This challenge is imposing enough for larger organizations with dedicated IT teams. It is basically impossible for leanly resourced small- and medium-sized businesses.
Because of this, our belief is that poor usability is the fundamental problem preventing widespread adoption of Zero Trust.
Simplifying the On-Ramp to Zero Trust
In our view, the core capabilities required to implement Zero Trust access controls are:
Support for secure connectivity to resources across public and private networks
Device awareness for any device type, whether virtual or physical, and whether mobile, desktop, or server
Stronger multi-factor identity authentication that ideally eliminates the need for passwords
Contextual awareness of location, usage patterns, and more
Workflow automation, visibility over network activity, and a policy engine to tie this all together
Today, these capabilities are distributed across multiple systems that are often challenging to procure, integrate, and orchestrate.
So how do we get started? In our conversations with hundreds of companies, one common pain point quickly emerged: can you help us eliminate our VPN?
With that insight, we launched Twingate with a clear and immediate value proposition to start: replace your VPN with a more secure, usable, and performant solution that your workforce will love.
As a VPN replacement, we offered customers:
A dramatically simpler deployment process, with an extensive API and automation capabilities for technical teams (who often bear the brunt of wrangling with VPNs)
Powerful security controls to provide granular access permissions and mitigate the risk of broad-based network access
More flexibility by decoupling access controls from network architectures
High performance, low latency connectivity for users through a combination of smart routing, split tunneling, direct peer-to-peer connections, and leveraging well-vetted transport protocols like QUIC
A seamless, set and forget experience for end users
In addition, we built deep integrations with your existing technology stack to make it easy to get started. These integrations in turn allowed our network connectivity layer to function as a simple orchestration engine across identities, devices, and context, regardless of where that information resides.
Very quickly, we saw customers using Twingate for much more than just a VPN replacement. Customers started using Twingate to implement ephemeral access controls, enforce device restrictions on SaaS apps, extend MFA to technical infrastructure, secure automated DevOps and Infrastructure-as-Code processes, and much more.
While early conversations about Twingate started with replacing VPNs, they very quickly evolved into how we actually presented an easy on-ramp to Zero Trust.
Embraced by Innovators
We’ve been humbled by the reception of Twingate since our launch 18 months ago. Companies of all sizes, from all over the world, have retired legacy network technologies like VPNs and NACs and started their Zero Trust journey with Twingate.

Today, Twingate is one of the highest-rated Zero Trust solutions on leading review sites like G2, and the winner of over 50 awards:

G2 Awards
To our customer community: we’re incredibly thankful for your tremendous support and inspiration. We’re excited to invest even more to deliver on the trust you’ve placed in us.
What’s Next
Looking ahead, our goal is to accelerate the adoption of Zero Trust by organizations around the world.
We plan to continue working to make Twingate simple enough for small businesses, yet powerful enough for the largest global enterprises, with accessible pricing plans to fit any budget (or no budget at all).
Here’s what you’ll see us investing in over the next year:
Doubling down on our distributed networking platform to provide the fastest, lowest latency connectivity experience for users in any network environment.
Extending the capabilities of our device agents to introduce device awareness and enable better access and authorization decisions based on rich, contextual device information.
Leveraging that device awareness to reimagine the authentication experience so we can reduce the reliance on passwords, improving security and reducing friction for users.
Providing extensive workflow automation, visibility, and seamless integrations with existing security solutions to unburden IT and Security teams.
If our mission is exciting to you, join us! We’re hiring across the company.
If you’re exploring Zero Trust for your company, try Twingate for free today.
If you’re a channel partner or MSP, join the Twingate Partner Alliance.
We’re excited to get to work. Let’s go!
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Solving the usability problem to unlock Zero Trust adoption
Tony Huie
•
Apr 14, 2022
Security has a usability problem.
When given a choice between security and convenience, people almost always choose the latter. As a result, security products that add too much friction, complexity, and frustration end up ineffective. This observation might sound obvious, but user-centric design is a rarity in the security space.
When we started Twingate a few years ago, we noticed that nowhere does security have a bigger usability problem than access control. On the surface, access appears to be a simple problem. But look at any company and you’ll see that access control is a complex orchestration of passwords, VPNs, NACs, etc. that is suboptimal for everyone involved.
So with usability as a focus, we set off to tackle this problem by focusing initially on designing a network access product that could be a simple yet powerful alternative to VPNs.
As it turns out, people really do care about good design. Since our launch 18 months ago, we’ve been humbled by the reception we’ve received from organizations and users all over the world.
Today, we’re excited to share that we’ve raised $42 million in Series B funding led by BOND, with significant participation from our existing investors WndrCo, 8VC, and SignalFire. We’re excited to welcome Jay Simons from BOND to a seasoned investor group that has built and backed some of the most successful software companies in the world. Jay joined Atlassian when it was the size of Twingate today, and built a pioneering product-driven model that enabled Atlassian to become one of the most widely used software platforms in the world. We couldn’t imagine a better partner to guide us as we build Twingate.
With this new round of funding, we’ll be investing aggressively to scale our team to meet the demands of our rapidly growing global customer base. In addition, we’re excited to announce two new programs:
The Twingate Partner Alliance, which will enable us to work even more closely with MSPs, resellers, and ISVs. We already work with many partners around the world, and we’re excited to invest even more heavily in our partner community.
The Twingate Starter Plan, a new, fully-free tier for any individual or organization to get started with Twingate, regardless of budget. Whether you’re a startup, hobbyist, or a Fortune 500 company, we want to make Twingate the most accessible platform for securing access to your private resources.
We’re just getting started and also wanted to take the opportunity to share what we’re building towards in the coming years.
Access Control is the Cybersecurity Imperative of the Next Decade
If you talk to buyers, vendors, and analysts in the IT and security industry, you’ll find no shortage of products for today’s security challenges. That in itself poses a challenge for companies. With security breaches growing in frequency and severity, security and IT teams are forced to string together an alphabet soup of complex tools that aren’t designed to work well together.
As a result, users often end up with the burden of making the difficult choice between security and convenience (and are then chastised when they inevitably opt for convenience).
At the root of this problem is a brittle access control model that was designed in the 1990s and has not evolved to meet the demands of modern work. Even for their most important resources, companies typically manage access through some combination of:
Static usernames and passwords;
Private, protected networks tied to physical locations (aka offices); and
Strictly managed devices (often coupled with VPN access for remote access into those networks).

VPN Traditional Remote Access Model
However, all of today’s user behaviors illustrate the shortcomings of this model:
Two-thirds of users admit to reusing passwords (and that’s just those who admit it!), which results in password compromises being one of the most common ways companies are breached.
Users can no longer be assumed to work from protected, company-controlled networks. People now work from everywhere, accessing corporate resources through all types of networks (home, coffee shops, airports, etc).
People use multiple devices for work (including BYOD/personal devices) and access cloud-based/SaaS services that can be accessed from anywhere, without a VPN.
Moreover, the tools and practices used to enforce this model create friction and frustration for users. Clunky VPNs slow down network traffic, frequent password resets drive users crazy, manual IP address allow-listing is brittle and cumbersome, and device management products are too invasive for personal devices.
The unfortunate result is that users actively look to circumvent these security measures, IT & security teams are overstretched trying to mitigate these resulting behaviors, and ultimately companies aren’t protected.
At Twingate, we believe there’s a better way. There is a superior access control model that solves these challenges, and we see every company shifting to this model over the next decade: Zero Trust.
The Usability Problem Holding Back Zero Trust
If you speak to enough security and IT leaders about how to solve today’s security challenges, the conversation will invariably turn to Zero Trust. Popularized by companies like Google, this security framework has its roots in the earliest days of the internet and has been heralded by analysts for over a decade. Even the U.S. federal government has made Zero Trust an imperative across all its departments and agencies. So, you may wonder, given this history, why hasn’t Zero Trust been adopted more widely?
The challenge is that while Zero Trust has emerged as the consensus security model of the future, IT and security leaders will tell you it is extremely challenging to put into practice. It requires too much change management, too much manual orchestration of disparate tools, too many resources, and too much patience (given what’s expected to be a multi-year process).
Our mission at Twingate is to change that dynamic by dramatically simplifying the journey towards Zero Trust.
Another challenge is that Zero Trust is frequently misused in today’s noisy security market. So, let’s start with a clear definition of what Zero Trust means to us.
At its core, Zero Trust is about answering one very simple question for every access attempt:

Zero Trust Access Framework
However, this question is deceptively simple, because when you play it out in any typical organization, it becomes very complex, very fast. Is the user a full time employee, a contractor, or an automated service? Is the device a company device, personal device, or a server? Can you tell if a user and device pair is working in an office, at home, or in a public cloud environment? Do we allow access via SSO, MFA, or VPN?
And even when you have all of this information, how do you determine whether access should be granted immediately, routed for approval, or denied? How long should access be allowed? The permutations get unwieldy very quickly.
Moreover, when you need to string together 4-5 (or more) different tools to answer this question, you can begin to see how complicated this access control model can become in practice. User information is locked in an SSO or identity provider, device information is housed in a separate MDM or EDR system, and contextual information is spread out across multiple siloed products or cloistered in a SIEM.
Additionally, granting access often means orchestrating connections between those tools and network-based products like VPNs or NACs.
Unfortunately, none of these tools are designed to work together. The result is a mess of increasing complexity for admins and constant friction that gets in the way of user productivity.

Zero Trust Access Framework with Integrations
This challenge is imposing enough for larger organizations with dedicated IT teams. It is basically impossible for leanly resourced small- and medium-sized businesses.
Because of this, our belief is that poor usability is the fundamental problem preventing widespread adoption of Zero Trust.
Simplifying the On-Ramp to Zero Trust
In our view, the core capabilities required to implement Zero Trust access controls are:
Support for secure connectivity to resources across public and private networks
Device awareness for any device type, whether virtual or physical, and whether mobile, desktop, or server
Stronger multi-factor identity authentication that ideally eliminates the need for passwords
Contextual awareness of location, usage patterns, and more
Workflow automation, visibility over network activity, and a policy engine to tie this all together
Today, these capabilities are distributed across multiple systems that are often challenging to procure, integrate, and orchestrate.
So how do we get started? In our conversations with hundreds of companies, one common pain point quickly emerged: can you help us eliminate our VPN?
With that insight, we launched Twingate with a clear and immediate value proposition to start: replace your VPN with a more secure, usable, and performant solution that your workforce will love.
As a VPN replacement, we offered customers:
A dramatically simpler deployment process, with an extensive API and automation capabilities for technical teams (who often bear the brunt of wrangling with VPNs)
Powerful security controls to provide granular access permissions and mitigate the risk of broad-based network access
More flexibility by decoupling access controls from network architectures
High performance, low latency connectivity for users through a combination of smart routing, split tunneling, direct peer-to-peer connections, and leveraging well-vetted transport protocols like QUIC
A seamless, set and forget experience for end users
In addition, we built deep integrations with your existing technology stack to make it easy to get started. These integrations in turn allowed our network connectivity layer to function as a simple orchestration engine across identities, devices, and context, regardless of where that information resides.
Very quickly, we saw customers using Twingate for much more than just a VPN replacement. Customers started using Twingate to implement ephemeral access controls, enforce device restrictions on SaaS apps, extend MFA to technical infrastructure, secure automated DevOps and Infrastructure-as-Code processes, and much more.
While early conversations about Twingate started with replacing VPNs, they very quickly evolved into how we actually presented an easy on-ramp to Zero Trust.
Embraced by Innovators
We’ve been humbled by the reception of Twingate since our launch 18 months ago. Companies of all sizes, from all over the world, have retired legacy network technologies like VPNs and NACs and started their Zero Trust journey with Twingate.

Today, Twingate is one of the highest-rated Zero Trust solutions on leading review sites like G2, and the winner of over 50 awards:

G2 Awards
To our customer community: we’re incredibly thankful for your tremendous support and inspiration. We’re excited to invest even more to deliver on the trust you’ve placed in us.
What’s Next
Looking ahead, our goal is to accelerate the adoption of Zero Trust by organizations around the world.
We plan to continue working to make Twingate simple enough for small businesses, yet powerful enough for the largest global enterprises, with accessible pricing plans to fit any budget (or no budget at all).
Here’s what you’ll see us investing in over the next year:
Doubling down on our distributed networking platform to provide the fastest, lowest latency connectivity experience for users in any network environment.
Extending the capabilities of our device agents to introduce device awareness and enable better access and authorization decisions based on rich, contextual device information.
Leveraging that device awareness to reimagine the authentication experience so we can reduce the reliance on passwords, improving security and reducing friction for users.
Providing extensive workflow automation, visibility, and seamless integrations with existing security solutions to unburden IT and Security teams.
If our mission is exciting to you, join us! We’re hiring across the company.
If you’re exploring Zero Trust for your company, try Twingate for free today.
If you’re a channel partner or MSP, join the Twingate Partner Alliance.
We’re excited to get to work. Let’s go!
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions