Managing Cyberattack Risk: An Ounce of Prevention is Worth a Pound of Cure
Stuart Loh
•
•
Jun 15, 2021

This blog post was written in collaboration with Coalition, a leading cyber insurance and security company.
Cyberattacks are on the rise
Cyberattacks are increasing in frequency because they are a moneymaker for cyber criminals. Coalition’s claims team saw a 35% increase in the frequency of funds transfer fraud (FTF) in 2020, and much of it was driven by the 67% rise we saw in business email compromise (BEC) attacks. In an FTF attack the scammers either redirect a legitimate payment to an account they control or submit a fraudulent invoice for payment; in both cases, they are simply trying to trick a user into sending money where it doesn’t belong. Companies handling invoice submission or account changes via email are likely to be targeted for compromise since email is unpredictable — staff can change, business processes evolve, and unclear communications are all too commonplace.
Like many aspects of life, the COVID-19 pandemic impacted cyber attacks by changing the targets and methods used by attackers. Remote work allowed many businesses to continue operations but also opened up new vulnerabilities, particularly Microsoft Remote Desktop (RDP). While convenient, RDP creates significant risk to any business using it, and in fact, Coalition saw a 47% increase in ransomware attacks largely driven by insecure remote access!
The value of cyber insurance
Cybersecurity is all about managing risks to data and the information systems that process it. Security controls help you proactively reduce those risks, and cyber insurance is a way to protect yourself from extreme losses if those controls fail.
Coalition is more than just cyber insurance. We focus on holistic risk management because we believe that prevention is always the best option. Coalition’s approach to prevention includes:
Risk Assessment: to identify potentially vulnerable systems or data. A Coalition Risk Assessment (CRA) happens as soon as you apply for insurance, and our automated risk manager performs continuous scans for our policyholders to alert them to critical cybersecurity risks.
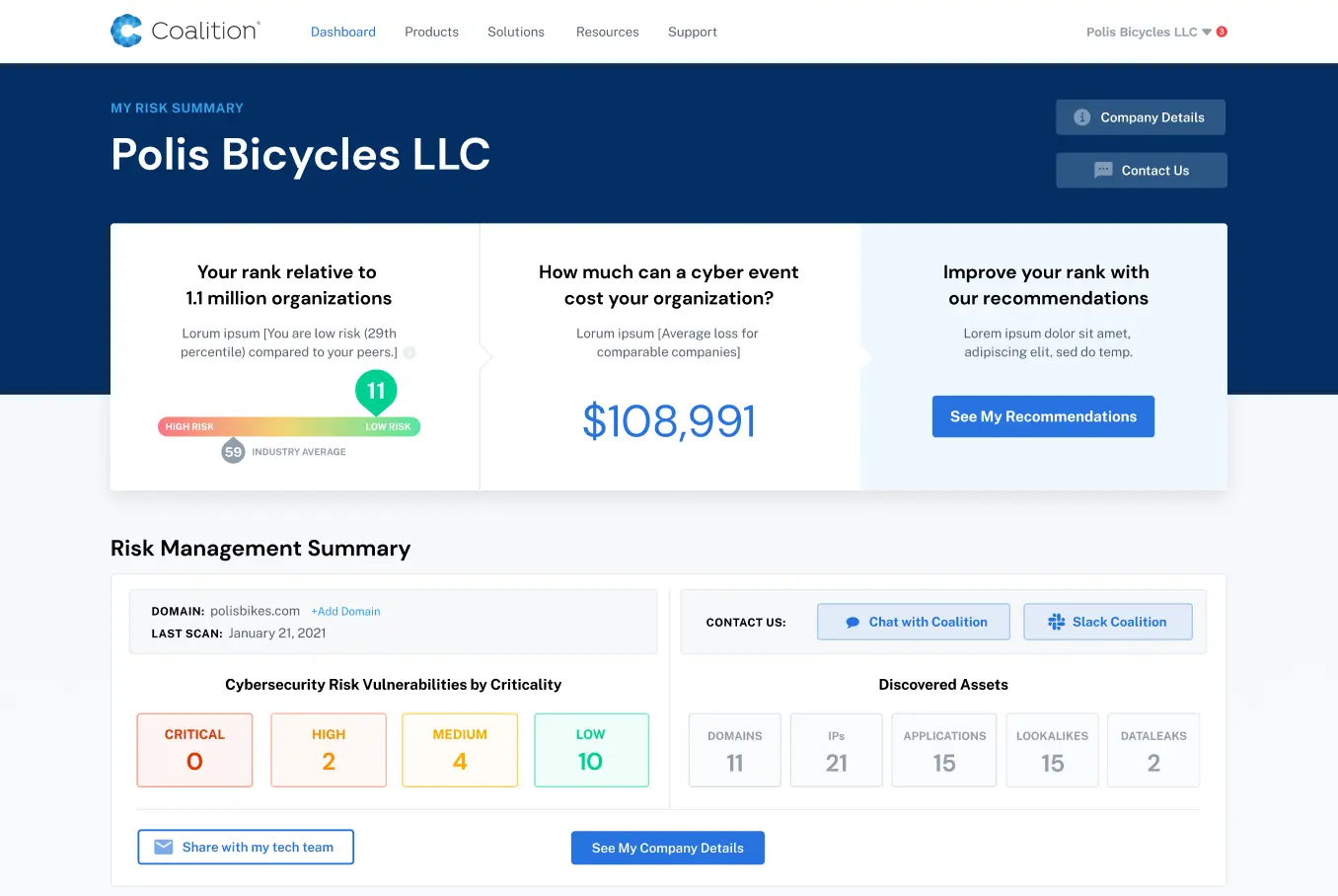
Knowledge: you can’t manage risks you don’t understand! Coalition offers a suite of knowledge resources including our help center and webinars to help our policyholders educate themselves on critical cybersecurity risk info!
Partners: identified risks must be addressed, and vetted partners like Twingate offer solutions to help deal with critical risks like secure remote access and zero trust architecture.
Even the best defenses can fail, and Coalition’s cyber insurance is a way to protect yourself if that occurs. Our dedicated claims and Coalition Incident Response teams are available 24/7 to help you navigate security incidents like ransomware, funds transfer fraud, and data breaches. We coordinate with law enforcement and financial institutions when needed, and our in-house incident response capabilities are unique in the cyber insurance industry.
Policyholders are more than just customers — they’re partners in solving cyber risk, and Coalition wants to keep conversations going rather than just being the call when something goes wrong. The combination of proactive risk mitigation and dedicated support during security incidents is unique, because unlike other cyber insurance carriers, you can report an incident to Coalition and get access to response services without triggering a claim! In fact, 45% of the time a policyholder contacts Coalition Claims, the incident is resolved without opening a claim. This benefits the insureds because it avoids expenses and the possibility of encountering difficulty getting insurance coverage in the future, which can be a consequence of filing a claim.
How Twingate helps to mitigate cybersecurity risk
As a solution for providing secure remote access to private corporate resources, Twingate occupies a critical role in any company’s cybersecurity infrastructure: ensuring that only properly authenticated users can access the resources they are supposed to access, and nothing more. Twingate fits into Coalition’s framework of holistic risk management by providing several important cyber risk mitigation benefits.
Enabling robust, least privilege access controls
Twingate applies modern Zero Trust Network Access principles to give businesses fine-grained control over what resources can be accessed by specific users, and under what conditions. Unlike VPNs (a widely used traditional remote access solution), access permissions are not coarsely granted to entire networks, but to specific resources, down to the level of individual ports. Control can be further honed with additional access requirements, such as device posture and location restrictions, empowering businesses to implement true “least privilege‚ access, a key risk management precept.
Twingate also integrates with major identity providers such as Okta, and allows their multi-factor authentication functionality to be extended beyond SaaS applications to any type of network resource.
Protecting against common network attacks
Twingate enables remote access into networks without exposing any ingress points to the public internet. Other services used for remote access, such as RDP and VPN gateways, act as lightning rods for attacks since they are often exposed directly to the internet. It has been widely reported that open RDP ports and VPN gateways are favored targets of attackers, who constantly probe them looking for vulnerabilities. By allowing a network to remain hidden, Twingate reduces the cyber attack surface area for businesses.
Moreover, due to Twingate’s Zero Trust architecture, should an attacker successfully gain access to a protected resource (such as by phishing or another social engineering attack), the potential scope of an incursion is limited to only the resources that the compromised user had access to. Contrast this to a VPN, where an incursion gives an attacker visibility across the entire network that the VPN protects. Twingate can limit the damage and liability caused by events such as ransomware attacks.
Providing visibility into network access activity
Data is key to detecting, mitigating, stopping, and remediating security breaches. Twingate can centrally log activity across a business’ entire network and ties each event to an identity — whether a user, device, or service — giving businesses unparalleled visibility and insight. This allows businesses to monitor for anomalous activity, understand how to mitigate or stop attacks in progress, and analyze breaches for post-incident debriefing and remediation so they don’t happen again.
How Coalition works with you and Twingate to secure your organization
Security controls provided by solutions like Twingate are essential for today’s businesses, but risk management does not end there. Cyber insurance is an important part of building a well-rounded approach to risk management and protecting you where security controls cannot. Learn how you can control your risk in minutes with Coalition.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Managing Cyberattack Risk: An Ounce of Prevention is Worth a Pound of Cure
Stuart Loh
•
•
Jun 15, 2021

This blog post was written in collaboration with Coalition, a leading cyber insurance and security company.
Cyberattacks are on the rise
Cyberattacks are increasing in frequency because they are a moneymaker for cyber criminals. Coalition’s claims team saw a 35% increase in the frequency of funds transfer fraud (FTF) in 2020, and much of it was driven by the 67% rise we saw in business email compromise (BEC) attacks. In an FTF attack the scammers either redirect a legitimate payment to an account they control or submit a fraudulent invoice for payment; in both cases, they are simply trying to trick a user into sending money where it doesn’t belong. Companies handling invoice submission or account changes via email are likely to be targeted for compromise since email is unpredictable — staff can change, business processes evolve, and unclear communications are all too commonplace.
Like many aspects of life, the COVID-19 pandemic impacted cyber attacks by changing the targets and methods used by attackers. Remote work allowed many businesses to continue operations but also opened up new vulnerabilities, particularly Microsoft Remote Desktop (RDP). While convenient, RDP creates significant risk to any business using it, and in fact, Coalition saw a 47% increase in ransomware attacks largely driven by insecure remote access!
The value of cyber insurance
Cybersecurity is all about managing risks to data and the information systems that process it. Security controls help you proactively reduce those risks, and cyber insurance is a way to protect yourself from extreme losses if those controls fail.
Coalition is more than just cyber insurance. We focus on holistic risk management because we believe that prevention is always the best option. Coalition’s approach to prevention includes:
Risk Assessment: to identify potentially vulnerable systems or data. A Coalition Risk Assessment (CRA) happens as soon as you apply for insurance, and our automated risk manager performs continuous scans for our policyholders to alert them to critical cybersecurity risks.

Knowledge: you can’t manage risks you don’t understand! Coalition offers a suite of knowledge resources including our help center and webinars to help our policyholders educate themselves on critical cybersecurity risk info!
Partners: identified risks must be addressed, and vetted partners like Twingate offer solutions to help deal with critical risks like secure remote access and zero trust architecture.
Even the best defenses can fail, and Coalition’s cyber insurance is a way to protect yourself if that occurs. Our dedicated claims and Coalition Incident Response teams are available 24/7 to help you navigate security incidents like ransomware, funds transfer fraud, and data breaches. We coordinate with law enforcement and financial institutions when needed, and our in-house incident response capabilities are unique in the cyber insurance industry.
Policyholders are more than just customers — they’re partners in solving cyber risk, and Coalition wants to keep conversations going rather than just being the call when something goes wrong. The combination of proactive risk mitigation and dedicated support during security incidents is unique, because unlike other cyber insurance carriers, you can report an incident to Coalition and get access to response services without triggering a claim! In fact, 45% of the time a policyholder contacts Coalition Claims, the incident is resolved without opening a claim. This benefits the insureds because it avoids expenses and the possibility of encountering difficulty getting insurance coverage in the future, which can be a consequence of filing a claim.
How Twingate helps to mitigate cybersecurity risk
As a solution for providing secure remote access to private corporate resources, Twingate occupies a critical role in any company’s cybersecurity infrastructure: ensuring that only properly authenticated users can access the resources they are supposed to access, and nothing more. Twingate fits into Coalition’s framework of holistic risk management by providing several important cyber risk mitigation benefits.
Enabling robust, least privilege access controls
Twingate applies modern Zero Trust Network Access principles to give businesses fine-grained control over what resources can be accessed by specific users, and under what conditions. Unlike VPNs (a widely used traditional remote access solution), access permissions are not coarsely granted to entire networks, but to specific resources, down to the level of individual ports. Control can be further honed with additional access requirements, such as device posture and location restrictions, empowering businesses to implement true “least privilege‚ access, a key risk management precept.
Twingate also integrates with major identity providers such as Okta, and allows their multi-factor authentication functionality to be extended beyond SaaS applications to any type of network resource.
Protecting against common network attacks
Twingate enables remote access into networks without exposing any ingress points to the public internet. Other services used for remote access, such as RDP and VPN gateways, act as lightning rods for attacks since they are often exposed directly to the internet. It has been widely reported that open RDP ports and VPN gateways are favored targets of attackers, who constantly probe them looking for vulnerabilities. By allowing a network to remain hidden, Twingate reduces the cyber attack surface area for businesses.
Moreover, due to Twingate’s Zero Trust architecture, should an attacker successfully gain access to a protected resource (such as by phishing or another social engineering attack), the potential scope of an incursion is limited to only the resources that the compromised user had access to. Contrast this to a VPN, where an incursion gives an attacker visibility across the entire network that the VPN protects. Twingate can limit the damage and liability caused by events such as ransomware attacks.
Providing visibility into network access activity
Data is key to detecting, mitigating, stopping, and remediating security breaches. Twingate can centrally log activity across a business’ entire network and ties each event to an identity — whether a user, device, or service — giving businesses unparalleled visibility and insight. This allows businesses to monitor for anomalous activity, understand how to mitigate or stop attacks in progress, and analyze breaches for post-incident debriefing and remediation so they don’t happen again.
How Coalition works with you and Twingate to secure your organization
Security controls provided by solutions like Twingate are essential for today’s businesses, but risk management does not end there. Cyber insurance is an important part of building a well-rounded approach to risk management and protecting you where security controls cannot. Learn how you can control your risk in minutes with Coalition.
Managing Cyberattack Risk: An Ounce of Prevention is Worth a Pound of Cure
Stuart Loh
•
•
Jun 15, 2021

This blog post was written in collaboration with Coalition, a leading cyber insurance and security company.
Cyberattacks are on the rise
Cyberattacks are increasing in frequency because they are a moneymaker for cyber criminals. Coalition’s claims team saw a 35% increase in the frequency of funds transfer fraud (FTF) in 2020, and much of it was driven by the 67% rise we saw in business email compromise (BEC) attacks. In an FTF attack the scammers either redirect a legitimate payment to an account they control or submit a fraudulent invoice for payment; in both cases, they are simply trying to trick a user into sending money where it doesn’t belong. Companies handling invoice submission or account changes via email are likely to be targeted for compromise since email is unpredictable — staff can change, business processes evolve, and unclear communications are all too commonplace.
Like many aspects of life, the COVID-19 pandemic impacted cyber attacks by changing the targets and methods used by attackers. Remote work allowed many businesses to continue operations but also opened up new vulnerabilities, particularly Microsoft Remote Desktop (RDP). While convenient, RDP creates significant risk to any business using it, and in fact, Coalition saw a 47% increase in ransomware attacks largely driven by insecure remote access!
The value of cyber insurance
Cybersecurity is all about managing risks to data and the information systems that process it. Security controls help you proactively reduce those risks, and cyber insurance is a way to protect yourself from extreme losses if those controls fail.
Coalition is more than just cyber insurance. We focus on holistic risk management because we believe that prevention is always the best option. Coalition’s approach to prevention includes:
Risk Assessment: to identify potentially vulnerable systems or data. A Coalition Risk Assessment (CRA) happens as soon as you apply for insurance, and our automated risk manager performs continuous scans for our policyholders to alert them to critical cybersecurity risks.

Knowledge: you can’t manage risks you don’t understand! Coalition offers a suite of knowledge resources including our help center and webinars to help our policyholders educate themselves on critical cybersecurity risk info!
Partners: identified risks must be addressed, and vetted partners like Twingate offer solutions to help deal with critical risks like secure remote access and zero trust architecture.
Even the best defenses can fail, and Coalition’s cyber insurance is a way to protect yourself if that occurs. Our dedicated claims and Coalition Incident Response teams are available 24/7 to help you navigate security incidents like ransomware, funds transfer fraud, and data breaches. We coordinate with law enforcement and financial institutions when needed, and our in-house incident response capabilities are unique in the cyber insurance industry.
Policyholders are more than just customers — they’re partners in solving cyber risk, and Coalition wants to keep conversations going rather than just being the call when something goes wrong. The combination of proactive risk mitigation and dedicated support during security incidents is unique, because unlike other cyber insurance carriers, you can report an incident to Coalition and get access to response services without triggering a claim! In fact, 45% of the time a policyholder contacts Coalition Claims, the incident is resolved without opening a claim. This benefits the insureds because it avoids expenses and the possibility of encountering difficulty getting insurance coverage in the future, which can be a consequence of filing a claim.
How Twingate helps to mitigate cybersecurity risk
As a solution for providing secure remote access to private corporate resources, Twingate occupies a critical role in any company’s cybersecurity infrastructure: ensuring that only properly authenticated users can access the resources they are supposed to access, and nothing more. Twingate fits into Coalition’s framework of holistic risk management by providing several important cyber risk mitigation benefits.
Enabling robust, least privilege access controls
Twingate applies modern Zero Trust Network Access principles to give businesses fine-grained control over what resources can be accessed by specific users, and under what conditions. Unlike VPNs (a widely used traditional remote access solution), access permissions are not coarsely granted to entire networks, but to specific resources, down to the level of individual ports. Control can be further honed with additional access requirements, such as device posture and location restrictions, empowering businesses to implement true “least privilege‚ access, a key risk management precept.
Twingate also integrates with major identity providers such as Okta, and allows their multi-factor authentication functionality to be extended beyond SaaS applications to any type of network resource.
Protecting against common network attacks
Twingate enables remote access into networks without exposing any ingress points to the public internet. Other services used for remote access, such as RDP and VPN gateways, act as lightning rods for attacks since they are often exposed directly to the internet. It has been widely reported that open RDP ports and VPN gateways are favored targets of attackers, who constantly probe them looking for vulnerabilities. By allowing a network to remain hidden, Twingate reduces the cyber attack surface area for businesses.
Moreover, due to Twingate’s Zero Trust architecture, should an attacker successfully gain access to a protected resource (such as by phishing or another social engineering attack), the potential scope of an incursion is limited to only the resources that the compromised user had access to. Contrast this to a VPN, where an incursion gives an attacker visibility across the entire network that the VPN protects. Twingate can limit the damage and liability caused by events such as ransomware attacks.
Providing visibility into network access activity
Data is key to detecting, mitigating, stopping, and remediating security breaches. Twingate can centrally log activity across a business’ entire network and ties each event to an identity — whether a user, device, or service — giving businesses unparalleled visibility and insight. This allows businesses to monitor for anomalous activity, understand how to mitigate or stop attacks in progress, and analyze breaches for post-incident debriefing and remediation so they don’t happen again.
How Coalition works with you and Twingate to secure your organization
Security controls provided by solutions like Twingate are essential for today’s businesses, but risk management does not end there. Cyber insurance is an important part of building a well-rounded approach to risk management and protecting you where security controls cannot. Learn how you can control your risk in minutes with Coalition.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Solutions
The VPN replacement your workforce will love.
Solutions
Solutions