Intro to Information Security & Compliance for IT Teams
Stuart Loh
•
•
Mar 23, 2021

Information security or cybersecurity compliance is an increasingly important part of business in the information age. While you’re probably familiar with general infosec standards like ISO 27001, what about specialized infosec standards like PCI DSS and the HIPAA Security Rule, and standards that don’t appear to be related to cybersecurity, but actually have a significant infosec component to them, like CCPA and GDPR?
Today there is an overwhelming array of global and regional compliance certifications, frameworks, standards, and regulations that companies need to sort through (for convenience, we use the term “compliance standard‚ to refer to all of these). APPs, CCPA, CIS, COPPA, CSA, FedRAMP, FERPA, FISMA, ISO, GDPR, HIPAA, NIST, PCI DSS, SOC, SOX, and the list goes on… Many of these acronyms don’t exclusively deal with security, but all of them have a security component to them. So where do you begin?
Introducing the Twingate Infosec Compliance Series
Over the coming weeks, we’ll be publishing a series of blog posts about security compliance that’s aimed at IT admins, security ops, and anyone else who is tasked with managing the implementation of infosec requirements imposed by compliance standards. We hope these articles will be especially useful to growing companies which may not have any dedicated compliance personnel.
First, we need to discuss why compliance is important (beyond compliance for compliance’s sake), and how to think about which compliance standards to tackle from the alphabet soup of standards. In our next post, we will describe a standard approach for tackling compliance, and future articles will demystify individual compliance standards to give you some high level context as an IT security professional and relate them to your responsibilities with infosec.
Why is compliance important?
Compliance has a reputation for being dry, busy work that rarely inspires enthusiasm in an organization. Part of this is due to the imposing laundry list of requirements that need to be satisfied when tackling a new compliance project.
Meeting these requirements often adds more work on top of your existing “day job.‚ Suddenly, you’re being asked to write security policies and procedures for everything, run an annual security training program, review ACLs every quarter, test out your disaster recovery plan, figure out how to implement an IDS, sit through endless compliance meetings, and more. Why are you being asked to do all of this stuff now?
The obvious reason is that compliance is often legally mandatory. Failure to comply means that the company and its employees are exposed to liability in the form of fines, court orders, or even consent decrees that can subject companies to 20 years of audits imposed by the FTC. In some cases, compliance failures could subject some employees to criminal liability.
Ok, but does compliance actually help? Or is this just “compliance for compliance’s sake‚? Beyond doing compliance just because “the law says so,‚ scary fines, or the fact that your manager made it a key deliverable for your next performance review, there are actually very good reasons why you personally should care:
Compliance reduces risk in a structured way. Taken as a whole, infosec compliance programs provide a comprehensive, methodical approach to securing an organization across all areas - from network security and access controls, to cybersecurity and risk management. This helps to eliminate blind spots in your overall infosec posture.
Compliance helps you win customers. Customers want to work with suppliers that they can trust. It’s now very common for customers to perform security assessment on potential vendors, and being able to demonstrate compliance makes you a less risky and more attractive business partner. In some cases, not being compliant with the standards a customer cares about will be a deal breaker. Infosec compliance is not just a cost — it can unlock new revenue!
Compliance means less fire fighting in the future. Once an infosec standard is implemented, it should reduce risk for your business, which means less time spent fighting fires in the future in the form of data breaches or other security incidents. Fires can be incredibly disruptive because they interrupt all of your other work.
Lead by example. For compliance to be effective, it needs to be part of an organization’s culture - you have to get everyone else to understand and care about it so they’re not encouraged to cut corners. As the overseer of infosec in your organization, that starts with you: you’re in the driver’s seat for educating and communicating why people need to pay attention to the measures you’ve invested painstaking hours implementing.
Compliance protects the reputation of your team and company. As Warren Buffett has famously said “It takes 20 years to build a reputation and five minutes to ruin it. If you think about that, you’ll do things differently.‚
When do you need to start thinking about compliance?
Compliance affects all businesses, no matter the size, and getting started as early as possible will benefit you in the long run. If you’re a lean startup, staring down a long list of infosec requirements may seem imposing, but you have the advantage of being nimble - for example, everyone who needs to be involved can likely fit around a small table. Moreover, once you attain compliance, maintaining it as your business grows tends to be a lighter lift and less disruptive than starting from scratch.
What do you need to comply with?
There are a bewildering number of compliance standards out there (see below for a handy list we compiled), and you may be getting pressure to implement a whole bunch of them because your lawyers or your sales team are telling you so.
But, you can’t do it all at once. If you are starting your compliance journey or operate a lean team, limited resources mean that you won’t be able to tackle more than one or perhaps two compliance projects at a time. This means you have to be judicious about prioritizing. How should you think about doing that? Here’s how we approach things at Twingate:
Start with mandatory compliance standards. Standards can be mandatory or voluntary, and it won’t be a surprise that you should start by complying with the ones you legally need to. For example, operating in the EU typically requires GDPR compliance. You should consult a lawyer or a security expert to understand what’s required for your specific business.
Rank other standards based on sales needs and business resources. Typically, your sales and marketing strategy, tempered by how onerous a standard is to comply with, will determine this ranking.
Business Needs
Compliance standards range from global, general standards (like ISO 27001 certification), to regional, industry-specific standards (like FERPA, which covers the U.S. education sector). Generally, you’ll get more bang for your buck implementing widely applicable global, general standards. But who and where your customers are will ultimately drive what’s most worthwhile to tackle next.
For instance, if your customers are mainly from a heavily regulated industry (and you’re not), you will likely be asked to comply with standards from their industry to be able to do business with them (e.g. GLBA for financial institutions, and HIPAA for healthcare providers). If you want to start doing business in the EU market, you will want to prioritize EU-specific standards like GDPR and PSD2. Often it makes sense to deprioritize standards that have narrow applicability.
If you’re a B2B company, you’ll want to focus on security standards that customers commonly ask you for, such as SOC 2 reports, ISO certifications, or standardized security questionnaires like the CSA CAIQ or VSA Questionnaire.
If you’re a B2C company, you’ll probably want to focus on standards relating to the protection of personal information, like CCPA and GDPR.
Business Resources
While there can be substantial overlap between the infosec requirements in different compliance standards, no two standards are quite alike. When assessing how much effort a compliance standard demands, think about it along these dimensions:
Prescriptiveness. Some standards are very prescriptive about the security measures you need to implement. For example, the infosec requirements in PCI DSS v3.2.1 span over 100 pages, with items down to the level of “perform quarterly external vulnerability scans, via an Approved Scanning Vendor.‚ On the other side of the spectrum, non-prescriptive standards (such as that contained in article 32 of the GDPR) mandate an “appropriate‚ or “reasonable‚ level of security, but don’t specify the exact measures required. Non-prescriptive standards offer more flexibility and may be less work for organizations with smaller or simpler operations.
Certifications. Some standards require official “certification‚ (e.g. SOC 2 reports), which typically involves an audit by an independent third party to verify you meet all applicable requirements. This tends to involve more time and expense since you need to pay for an annual audit.
Overlapping Requirements. As mentioned above, infosec requirements can overlap between different standards (e.g. minimum complexity requirements for passwords is an extremely common requirement). As you comply with more and more standards, the hard work you do compounds, and you will find that complying with each additional standard requires less work because you’ve already satisfied the same infosec requirements from a previous project. Consider performing a requirements mapping exercise between standards to understand the extent of the overlap.
What are all the standards?
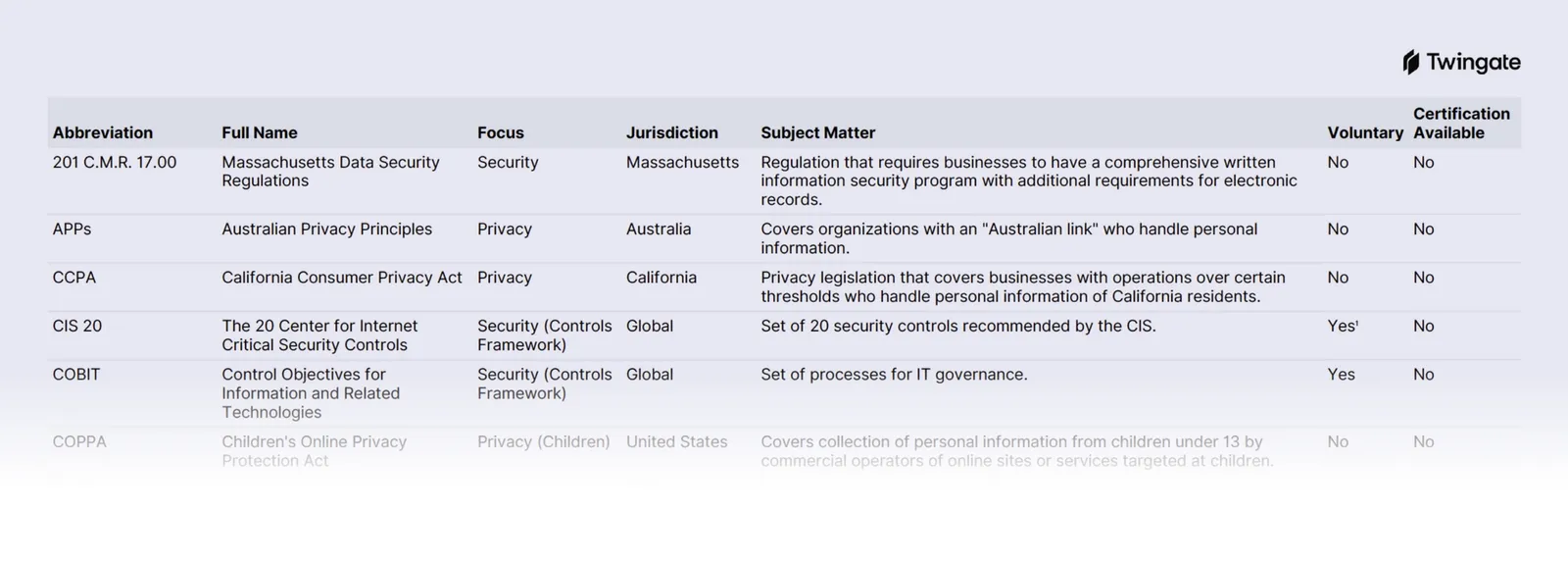
There are a ton of compliance standards that have an infosec aspect to them. If you’re curious about what they all are, we’ve compiled this useful chart. It’s not comprehensive by any means, but it covers a lot of them.
What’s next?
Now that you have a ranked list of standards you want to meet, what now? The next post in the series will discuss an approach to attaining any compliance standard.
Infosec Compliance Series
The Infosec Compliance Series comprises the articles below. This list will be updated each time we publish a new article. To be notified about new articles, subscribe to this blog’s RSS feed.
Intro to Information Security & Compliance for IT Teams (this article)
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Intro to Information Security & Compliance for IT Teams
Stuart Loh
•
•
Mar 23, 2021

Information security or cybersecurity compliance is an increasingly important part of business in the information age. While you’re probably familiar with general infosec standards like ISO 27001, what about specialized infosec standards like PCI DSS and the HIPAA Security Rule, and standards that don’t appear to be related to cybersecurity, but actually have a significant infosec component to them, like CCPA and GDPR?
Today there is an overwhelming array of global and regional compliance certifications, frameworks, standards, and regulations that companies need to sort through (for convenience, we use the term “compliance standard‚ to refer to all of these). APPs, CCPA, CIS, COPPA, CSA, FedRAMP, FERPA, FISMA, ISO, GDPR, HIPAA, NIST, PCI DSS, SOC, SOX, and the list goes on… Many of these acronyms don’t exclusively deal with security, but all of them have a security component to them. So where do you begin?
Introducing the Twingate Infosec Compliance Series
Over the coming weeks, we’ll be publishing a series of blog posts about security compliance that’s aimed at IT admins, security ops, and anyone else who is tasked with managing the implementation of infosec requirements imposed by compliance standards. We hope these articles will be especially useful to growing companies which may not have any dedicated compliance personnel.
First, we need to discuss why compliance is important (beyond compliance for compliance’s sake), and how to think about which compliance standards to tackle from the alphabet soup of standards. In our next post, we will describe a standard approach for tackling compliance, and future articles will demystify individual compliance standards to give you some high level context as an IT security professional and relate them to your responsibilities with infosec.
Why is compliance important?
Compliance has a reputation for being dry, busy work that rarely inspires enthusiasm in an organization. Part of this is due to the imposing laundry list of requirements that need to be satisfied when tackling a new compliance project.
Meeting these requirements often adds more work on top of your existing “day job.‚ Suddenly, you’re being asked to write security policies and procedures for everything, run an annual security training program, review ACLs every quarter, test out your disaster recovery plan, figure out how to implement an IDS, sit through endless compliance meetings, and more. Why are you being asked to do all of this stuff now?
The obvious reason is that compliance is often legally mandatory. Failure to comply means that the company and its employees are exposed to liability in the form of fines, court orders, or even consent decrees that can subject companies to 20 years of audits imposed by the FTC. In some cases, compliance failures could subject some employees to criminal liability.
Ok, but does compliance actually help? Or is this just “compliance for compliance’s sake‚? Beyond doing compliance just because “the law says so,‚ scary fines, or the fact that your manager made it a key deliverable for your next performance review, there are actually very good reasons why you personally should care:
Compliance reduces risk in a structured way. Taken as a whole, infosec compliance programs provide a comprehensive, methodical approach to securing an organization across all areas - from network security and access controls, to cybersecurity and risk management. This helps to eliminate blind spots in your overall infosec posture.
Compliance helps you win customers. Customers want to work with suppliers that they can trust. It’s now very common for customers to perform security assessment on potential vendors, and being able to demonstrate compliance makes you a less risky and more attractive business partner. In some cases, not being compliant with the standards a customer cares about will be a deal breaker. Infosec compliance is not just a cost — it can unlock new revenue!
Compliance means less fire fighting in the future. Once an infosec standard is implemented, it should reduce risk for your business, which means less time spent fighting fires in the future in the form of data breaches or other security incidents. Fires can be incredibly disruptive because they interrupt all of your other work.
Lead by example. For compliance to be effective, it needs to be part of an organization’s culture - you have to get everyone else to understand and care about it so they’re not encouraged to cut corners. As the overseer of infosec in your organization, that starts with you: you’re in the driver’s seat for educating and communicating why people need to pay attention to the measures you’ve invested painstaking hours implementing.
Compliance protects the reputation of your team and company. As Warren Buffett has famously said “It takes 20 years to build a reputation and five minutes to ruin it. If you think about that, you’ll do things differently.‚
When do you need to start thinking about compliance?
Compliance affects all businesses, no matter the size, and getting started as early as possible will benefit you in the long run. If you’re a lean startup, staring down a long list of infosec requirements may seem imposing, but you have the advantage of being nimble - for example, everyone who needs to be involved can likely fit around a small table. Moreover, once you attain compliance, maintaining it as your business grows tends to be a lighter lift and less disruptive than starting from scratch.
What do you need to comply with?
There are a bewildering number of compliance standards out there (see below for a handy list we compiled), and you may be getting pressure to implement a whole bunch of them because your lawyers or your sales team are telling you so.
But, you can’t do it all at once. If you are starting your compliance journey or operate a lean team, limited resources mean that you won’t be able to tackle more than one or perhaps two compliance projects at a time. This means you have to be judicious about prioritizing. How should you think about doing that? Here’s how we approach things at Twingate:
Start with mandatory compliance standards. Standards can be mandatory or voluntary, and it won’t be a surprise that you should start by complying with the ones you legally need to. For example, operating in the EU typically requires GDPR compliance. You should consult a lawyer or a security expert to understand what’s required for your specific business.
Rank other standards based on sales needs and business resources. Typically, your sales and marketing strategy, tempered by how onerous a standard is to comply with, will determine this ranking.
Business Needs
Compliance standards range from global, general standards (like ISO 27001 certification), to regional, industry-specific standards (like FERPA, which covers the U.S. education sector). Generally, you’ll get more bang for your buck implementing widely applicable global, general standards. But who and where your customers are will ultimately drive what’s most worthwhile to tackle next.
For instance, if your customers are mainly from a heavily regulated industry (and you’re not), you will likely be asked to comply with standards from their industry to be able to do business with them (e.g. GLBA for financial institutions, and HIPAA for healthcare providers). If you want to start doing business in the EU market, you will want to prioritize EU-specific standards like GDPR and PSD2. Often it makes sense to deprioritize standards that have narrow applicability.
If you’re a B2B company, you’ll want to focus on security standards that customers commonly ask you for, such as SOC 2 reports, ISO certifications, or standardized security questionnaires like the CSA CAIQ or VSA Questionnaire.
If you’re a B2C company, you’ll probably want to focus on standards relating to the protection of personal information, like CCPA and GDPR.
Business Resources
While there can be substantial overlap between the infosec requirements in different compliance standards, no two standards are quite alike. When assessing how much effort a compliance standard demands, think about it along these dimensions:
Prescriptiveness. Some standards are very prescriptive about the security measures you need to implement. For example, the infosec requirements in PCI DSS v3.2.1 span over 100 pages, with items down to the level of “perform quarterly external vulnerability scans, via an Approved Scanning Vendor.‚ On the other side of the spectrum, non-prescriptive standards (such as that contained in article 32 of the GDPR) mandate an “appropriate‚ or “reasonable‚ level of security, but don’t specify the exact measures required. Non-prescriptive standards offer more flexibility and may be less work for organizations with smaller or simpler operations.
Certifications. Some standards require official “certification‚ (e.g. SOC 2 reports), which typically involves an audit by an independent third party to verify you meet all applicable requirements. This tends to involve more time and expense since you need to pay for an annual audit.
Overlapping Requirements. As mentioned above, infosec requirements can overlap between different standards (e.g. minimum complexity requirements for passwords is an extremely common requirement). As you comply with more and more standards, the hard work you do compounds, and you will find that complying with each additional standard requires less work because you’ve already satisfied the same infosec requirements from a previous project. Consider performing a requirements mapping exercise between standards to understand the extent of the overlap.
What are all the standards?

There are a ton of compliance standards that have an infosec aspect to them. If you’re curious about what they all are, we’ve compiled this useful chart. It’s not comprehensive by any means, but it covers a lot of them.
What’s next?
Now that you have a ranked list of standards you want to meet, what now? The next post in the series will discuss an approach to attaining any compliance standard.
Infosec Compliance Series
The Infosec Compliance Series comprises the articles below. This list will be updated each time we publish a new article. To be notified about new articles, subscribe to this blog’s RSS feed.
Intro to Information Security & Compliance for IT Teams (this article)
Intro to Information Security & Compliance for IT Teams
Stuart Loh
•
•
Mar 23, 2021

Information security or cybersecurity compliance is an increasingly important part of business in the information age. While you’re probably familiar with general infosec standards like ISO 27001, what about specialized infosec standards like PCI DSS and the HIPAA Security Rule, and standards that don’t appear to be related to cybersecurity, but actually have a significant infosec component to them, like CCPA and GDPR?
Today there is an overwhelming array of global and regional compliance certifications, frameworks, standards, and regulations that companies need to sort through (for convenience, we use the term “compliance standard‚ to refer to all of these). APPs, CCPA, CIS, COPPA, CSA, FedRAMP, FERPA, FISMA, ISO, GDPR, HIPAA, NIST, PCI DSS, SOC, SOX, and the list goes on… Many of these acronyms don’t exclusively deal with security, but all of them have a security component to them. So where do you begin?
Introducing the Twingate Infosec Compliance Series
Over the coming weeks, we’ll be publishing a series of blog posts about security compliance that’s aimed at IT admins, security ops, and anyone else who is tasked with managing the implementation of infosec requirements imposed by compliance standards. We hope these articles will be especially useful to growing companies which may not have any dedicated compliance personnel.
First, we need to discuss why compliance is important (beyond compliance for compliance’s sake), and how to think about which compliance standards to tackle from the alphabet soup of standards. In our next post, we will describe a standard approach for tackling compliance, and future articles will demystify individual compliance standards to give you some high level context as an IT security professional and relate them to your responsibilities with infosec.
Why is compliance important?
Compliance has a reputation for being dry, busy work that rarely inspires enthusiasm in an organization. Part of this is due to the imposing laundry list of requirements that need to be satisfied when tackling a new compliance project.
Meeting these requirements often adds more work on top of your existing “day job.‚ Suddenly, you’re being asked to write security policies and procedures for everything, run an annual security training program, review ACLs every quarter, test out your disaster recovery plan, figure out how to implement an IDS, sit through endless compliance meetings, and more. Why are you being asked to do all of this stuff now?
The obvious reason is that compliance is often legally mandatory. Failure to comply means that the company and its employees are exposed to liability in the form of fines, court orders, or even consent decrees that can subject companies to 20 years of audits imposed by the FTC. In some cases, compliance failures could subject some employees to criminal liability.
Ok, but does compliance actually help? Or is this just “compliance for compliance’s sake‚? Beyond doing compliance just because “the law says so,‚ scary fines, or the fact that your manager made it a key deliverable for your next performance review, there are actually very good reasons why you personally should care:
Compliance reduces risk in a structured way. Taken as a whole, infosec compliance programs provide a comprehensive, methodical approach to securing an organization across all areas - from network security and access controls, to cybersecurity and risk management. This helps to eliminate blind spots in your overall infosec posture.
Compliance helps you win customers. Customers want to work with suppliers that they can trust. It’s now very common for customers to perform security assessment on potential vendors, and being able to demonstrate compliance makes you a less risky and more attractive business partner. In some cases, not being compliant with the standards a customer cares about will be a deal breaker. Infosec compliance is not just a cost — it can unlock new revenue!
Compliance means less fire fighting in the future. Once an infosec standard is implemented, it should reduce risk for your business, which means less time spent fighting fires in the future in the form of data breaches or other security incidents. Fires can be incredibly disruptive because they interrupt all of your other work.
Lead by example. For compliance to be effective, it needs to be part of an organization’s culture - you have to get everyone else to understand and care about it so they’re not encouraged to cut corners. As the overseer of infosec in your organization, that starts with you: you’re in the driver’s seat for educating and communicating why people need to pay attention to the measures you’ve invested painstaking hours implementing.
Compliance protects the reputation of your team and company. As Warren Buffett has famously said “It takes 20 years to build a reputation and five minutes to ruin it. If you think about that, you’ll do things differently.‚
When do you need to start thinking about compliance?
Compliance affects all businesses, no matter the size, and getting started as early as possible will benefit you in the long run. If you’re a lean startup, staring down a long list of infosec requirements may seem imposing, but you have the advantage of being nimble - for example, everyone who needs to be involved can likely fit around a small table. Moreover, once you attain compliance, maintaining it as your business grows tends to be a lighter lift and less disruptive than starting from scratch.
What do you need to comply with?
There are a bewildering number of compliance standards out there (see below for a handy list we compiled), and you may be getting pressure to implement a whole bunch of them because your lawyers or your sales team are telling you so.
But, you can’t do it all at once. If you are starting your compliance journey or operate a lean team, limited resources mean that you won’t be able to tackle more than one or perhaps two compliance projects at a time. This means you have to be judicious about prioritizing. How should you think about doing that? Here’s how we approach things at Twingate:
Start with mandatory compliance standards. Standards can be mandatory or voluntary, and it won’t be a surprise that you should start by complying with the ones you legally need to. For example, operating in the EU typically requires GDPR compliance. You should consult a lawyer or a security expert to understand what’s required for your specific business.
Rank other standards based on sales needs and business resources. Typically, your sales and marketing strategy, tempered by how onerous a standard is to comply with, will determine this ranking.
Business Needs
Compliance standards range from global, general standards (like ISO 27001 certification), to regional, industry-specific standards (like FERPA, which covers the U.S. education sector). Generally, you’ll get more bang for your buck implementing widely applicable global, general standards. But who and where your customers are will ultimately drive what’s most worthwhile to tackle next.
For instance, if your customers are mainly from a heavily regulated industry (and you’re not), you will likely be asked to comply with standards from their industry to be able to do business with them (e.g. GLBA for financial institutions, and HIPAA for healthcare providers). If you want to start doing business in the EU market, you will want to prioritize EU-specific standards like GDPR and PSD2. Often it makes sense to deprioritize standards that have narrow applicability.
If you’re a B2B company, you’ll want to focus on security standards that customers commonly ask you for, such as SOC 2 reports, ISO certifications, or standardized security questionnaires like the CSA CAIQ or VSA Questionnaire.
If you’re a B2C company, you’ll probably want to focus on standards relating to the protection of personal information, like CCPA and GDPR.
Business Resources
While there can be substantial overlap between the infosec requirements in different compliance standards, no two standards are quite alike. When assessing how much effort a compliance standard demands, think about it along these dimensions:
Prescriptiveness. Some standards are very prescriptive about the security measures you need to implement. For example, the infosec requirements in PCI DSS v3.2.1 span over 100 pages, with items down to the level of “perform quarterly external vulnerability scans, via an Approved Scanning Vendor.‚ On the other side of the spectrum, non-prescriptive standards (such as that contained in article 32 of the GDPR) mandate an “appropriate‚ or “reasonable‚ level of security, but don’t specify the exact measures required. Non-prescriptive standards offer more flexibility and may be less work for organizations with smaller or simpler operations.
Certifications. Some standards require official “certification‚ (e.g. SOC 2 reports), which typically involves an audit by an independent third party to verify you meet all applicable requirements. This tends to involve more time and expense since you need to pay for an annual audit.
Overlapping Requirements. As mentioned above, infosec requirements can overlap between different standards (e.g. minimum complexity requirements for passwords is an extremely common requirement). As you comply with more and more standards, the hard work you do compounds, and you will find that complying with each additional standard requires less work because you’ve already satisfied the same infosec requirements from a previous project. Consider performing a requirements mapping exercise between standards to understand the extent of the overlap.
What are all the standards?

There are a ton of compliance standards that have an infosec aspect to them. If you’re curious about what they all are, we’ve compiled this useful chart. It’s not comprehensive by any means, but it covers a lot of them.
What’s next?
Now that you have a ranked list of standards you want to meet, what now? The next post in the series will discuss an approach to attaining any compliance standard.
Infosec Compliance Series
The Infosec Compliance Series comprises the articles below. This list will be updated each time we publish a new article. To be notified about new articles, subscribe to this blog’s RSS feed.
Intro to Information Security & Compliance for IT Teams (this article)
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Solutions
The VPN replacement your workforce will love.
Solutions
Solutions