Introducing Identity Firewall: Security, Performance, Simplicity. Pick Three.
Anna Liu
•
Head of Product
•
Nov 13, 2025

Identity-based access for users, services, and AI agents that deploys in minutes, scales to every resource, and finally lets you retire your VPN.
Explore documentation →
For decades, security teams have been forced to make impossible choices. Pick strong security, and watch development velocity crater under endless ticket queues and approval workflows. Optimize for performance, and accept the exposure that comes with overly broad access. Try to keep things simple, and sacrifice the granular controls that compliance demands.
Legacy security architectures - VPNs, traditional PAM solutions, jumpboxes - all suffer from the same fundamental flaw: they were designed for a world where infrastructure lived in one data center, developers sat in one office, and software was released quarterly. That world is gone.
Today's reality is starkly different. Your infrastructure spans multiple clouds. Your developers work from everywhere. Your applications ship continuously. And now, AI agents are joining the workforce: autonomous systems that need secure access to databases, APIs, and production environments without human intervention.
The old security playbook can't handle this. Traditional PAM solutions require months to deploy, cost upward of half a million dollars annually, and still only protect a handful of critical systems. VPNs grant network access when you need resource-level control. Jumpboxes create bottlenecks and single points of failure. And none of these solutions were designed with AI agents in mind.
That's why we built the Twingate Identity Firewall.
A New Approach to Privileged Access
Twingate Identity Firewall extends Zero Trust and Privileged Access Management controls to every user, resource, and agent in your organization, regardless of where they work. It unifies network access and privileged access into a single platform that's purpose-built for cloud-native, AI-powered development teams.
Here's what makes it different:
Unified Identity Enforcement
Your users authenticate once through your existing identity provider: Okta, Azure AD, Google Workspace, or any other SSO solution. That identity seamlessly passes through to every resource they access, from Kubernetes clusters to PostgreSQL databases to internal APIs. No more managing separate credentials for different systems. No more exposed public endpoints. Just identity-based access, everywhere.
Dynamic Zero-Standing Access
Access is granted just-in-time, based on identity, device posture, location, and contextual signals. Users and agents get exactly the permissions they need for exactly as long as they need them, then those permissions automatically disappear. Such ephemeral access dramatically reduces your attack surface without the friction of manual approval workflows or support tickets.
Complete Visibility and Control
Every command, every API call, every database query is tied to a specific user or agent with forensic-level detail. Session replay capabilities let you see exactly what happened during any access session. You need visibility for compliance, incident response, security operations, and knowledge sharing. You don’t need additional overhead.
Cost-Effective Scale
Deploy comprehensive privileged access controls across your entire environment at a fraction of traditional costs. Until now, the cost of expensive, duplicative controls makes protecting non-administrative users prohibitively expensive. No hardware appliances or complex infrastructure requirements. Just software that works for you.
Built for the Age of AI
AI is fundamentally changing how software gets built. Developers are using AI coding assistants that need access to codebases and deployment pipelines. AI agents are performing tasks that previously required human intervention, from infrastructure provisioning to data analysis to incident response. These agents need secure, identity-based access just like human users.
Twingate Identity Firewall is purpose-built for this agentic future. It extends the same Zero Trust principles to AI agents that you apply to human users, with planned support for emerging standards like the Model Context Protocol (MCP) and Agent-to-Agent (A2A) communication. This means your AI agents can work autonomously without compromising security.
We are on a mission: Our customers are building the AI infrastructure that will power a new tomorrow. Ophir Zahavi, Senior Cloud Engineering Manager at H2O.ai, puts it this way:
"At H2O.ai, we're all about democratizing AI. Twingate is a natural extension of that philosophy. It's the path of least resistance to least privilege access, allowing our globally distributed teams to get just-in-time access to what they need—whether it's an API, a Kubernetes cluster, or a Postgres database—without compromising our zero trust principles. It's security that truly enables developer speed at the scale we need for AI."
Like H2O.ai's approach to AI, we're looking to democratize privileged access.
Simplicity at Scale
The most powerful feature of Twingate Identity Firewall might be what it removes from your infrastructure. No jumpboxes to maintain. No VPN concentrators to scale. No complex firewall rule management. No manual credential rotation. No per-resource configuration overhead.
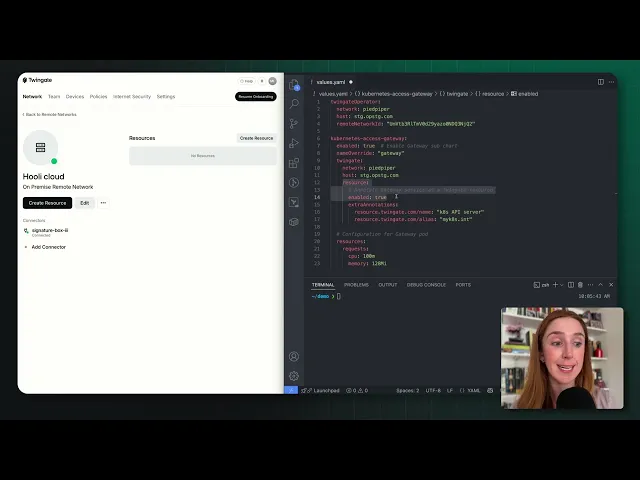
Deployment takes minutes instead of months. You connect Twingate to your identity provider, deploy lightweight connectors in your environments (they run anywhere: cloud VPCs, on-premises networks, Kubernetes clusters), and define access policies. That's it.
Because Twingate integrates natively with modern DevOps workflows, including infrastructure-as-code tools like Terraform and Pulumi, you can manage access policies the same way you manage infrastructure. API-first design means everything can be automated. And because access decisions happen before network traffic ever leaves a user's device, unauthorized access attempts never even reach your resources.
The result? Security teams get the granular control and visibility they need. Developers get fast, frictionless access to the resources they need. And IT teams finally get to sunset those legacy VPNs.
Getting Started
Twingate Identity Firewall is available now and works seamlessly with Twingate Private Access and Twingate Internet Security. Current support includes Kubernetes API and SSH. PostgreSQL and HTTPS sessions, with expanded protocol support and specific enhancements for Model Context Protocol (MCP) and Agent-to-Agent (A2A) workflows, are coming soon.
Organizations can start free with the Twingate Starter Plan, which includes Identity Firewall for up to 5 resources with no credit card required. From there, scaling to thousands of resources and users is just as simple.
The old trade-offs are over. You don't have to choose between security, performance, and simplicity anymore.
You can have all three.

New to Twingate? You can try out Twingate for free or request a personalized demo from our team.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Introducing Identity Firewall: Security, Performance, Simplicity. Pick Three.
Anna Liu
•
Head of Product
•
Nov 13, 2025

Identity-based access for users, services, and AI agents that deploys in minutes, scales to every resource, and finally lets you retire your VPN.
Explore documentation →
For decades, security teams have been forced to make impossible choices. Pick strong security, and watch development velocity crater under endless ticket queues and approval workflows. Optimize for performance, and accept the exposure that comes with overly broad access. Try to keep things simple, and sacrifice the granular controls that compliance demands.
Legacy security architectures - VPNs, traditional PAM solutions, jumpboxes - all suffer from the same fundamental flaw: they were designed for a world where infrastructure lived in one data center, developers sat in one office, and software was released quarterly. That world is gone.
Today's reality is starkly different. Your infrastructure spans multiple clouds. Your developers work from everywhere. Your applications ship continuously. And now, AI agents are joining the workforce: autonomous systems that need secure access to databases, APIs, and production environments without human intervention.
The old security playbook can't handle this. Traditional PAM solutions require months to deploy, cost upward of half a million dollars annually, and still only protect a handful of critical systems. VPNs grant network access when you need resource-level control. Jumpboxes create bottlenecks and single points of failure. And none of these solutions were designed with AI agents in mind.
That's why we built the Twingate Identity Firewall.
A New Approach to Privileged Access
Twingate Identity Firewall extends Zero Trust and Privileged Access Management controls to every user, resource, and agent in your organization, regardless of where they work. It unifies network access and privileged access into a single platform that's purpose-built for cloud-native, AI-powered development teams.
Here's what makes it different:
Unified Identity Enforcement
Your users authenticate once through your existing identity provider: Okta, Azure AD, Google Workspace, or any other SSO solution. That identity seamlessly passes through to every resource they access, from Kubernetes clusters to PostgreSQL databases to internal APIs. No more managing separate credentials for different systems. No more exposed public endpoints. Just identity-based access, everywhere.
Dynamic Zero-Standing Access
Access is granted just-in-time, based on identity, device posture, location, and contextual signals. Users and agents get exactly the permissions they need for exactly as long as they need them, then those permissions automatically disappear. Such ephemeral access dramatically reduces your attack surface without the friction of manual approval workflows or support tickets.
Complete Visibility and Control
Every command, every API call, every database query is tied to a specific user or agent with forensic-level detail. Session replay capabilities let you see exactly what happened during any access session. You need visibility for compliance, incident response, security operations, and knowledge sharing. You don’t need additional overhead.
Cost-Effective Scale
Deploy comprehensive privileged access controls across your entire environment at a fraction of traditional costs. Until now, the cost of expensive, duplicative controls makes protecting non-administrative users prohibitively expensive. No hardware appliances or complex infrastructure requirements. Just software that works for you.
Built for the Age of AI
AI is fundamentally changing how software gets built. Developers are using AI coding assistants that need access to codebases and deployment pipelines. AI agents are performing tasks that previously required human intervention, from infrastructure provisioning to data analysis to incident response. These agents need secure, identity-based access just like human users.
Twingate Identity Firewall is purpose-built for this agentic future. It extends the same Zero Trust principles to AI agents that you apply to human users, with planned support for emerging standards like the Model Context Protocol (MCP) and Agent-to-Agent (A2A) communication. This means your AI agents can work autonomously without compromising security.
We are on a mission: Our customers are building the AI infrastructure that will power a new tomorrow. Ophir Zahavi, Senior Cloud Engineering Manager at H2O.ai, puts it this way:
"At H2O.ai, we're all about democratizing AI. Twingate is a natural extension of that philosophy. It's the path of least resistance to least privilege access, allowing our globally distributed teams to get just-in-time access to what they need—whether it's an API, a Kubernetes cluster, or a Postgres database—without compromising our zero trust principles. It's security that truly enables developer speed at the scale we need for AI."
Like H2O.ai's approach to AI, we're looking to democratize privileged access.
Simplicity at Scale
The most powerful feature of Twingate Identity Firewall might be what it removes from your infrastructure. No jumpboxes to maintain. No VPN concentrators to scale. No complex firewall rule management. No manual credential rotation. No per-resource configuration overhead.
Deployment takes minutes instead of months. You connect Twingate to your identity provider, deploy lightweight connectors in your environments (they run anywhere: cloud VPCs, on-premises networks, Kubernetes clusters), and define access policies. That's it.
Because Twingate integrates natively with modern DevOps workflows, including infrastructure-as-code tools like Terraform and Pulumi, you can manage access policies the same way you manage infrastructure. API-first design means everything can be automated. And because access decisions happen before network traffic ever leaves a user's device, unauthorized access attempts never even reach your resources.
The result? Security teams get the granular control and visibility they need. Developers get fast, frictionless access to the resources they need. And IT teams finally get to sunset those legacy VPNs.
Getting Started
Twingate Identity Firewall is available now and works seamlessly with Twingate Private Access and Twingate Internet Security. Current support includes Kubernetes API and SSH. PostgreSQL and HTTPS sessions, with expanded protocol support and specific enhancements for Model Context Protocol (MCP) and Agent-to-Agent (A2A) workflows, are coming soon.
Organizations can start free with the Twingate Starter Plan, which includes Identity Firewall for up to 5 resources with no credit card required. From there, scaling to thousands of resources and users is just as simple.
The old trade-offs are over. You don't have to choose between security, performance, and simplicity anymore.
You can have all three.

New to Twingate? You can try out Twingate for free or request a personalized demo from our team.
Rapidly implement a modern Zero Trust network that is more secure and maintainable than VPNs.
Introducing Identity Firewall: Security, Performance, Simplicity. Pick Three.
Anna Liu
•
Head of Product
•
Nov 13, 2025

Identity-based access for users, services, and AI agents that deploys in minutes, scales to every resource, and finally lets you retire your VPN.
Explore documentation →
For decades, security teams have been forced to make impossible choices. Pick strong security, and watch development velocity crater under endless ticket queues and approval workflows. Optimize for performance, and accept the exposure that comes with overly broad access. Try to keep things simple, and sacrifice the granular controls that compliance demands.
Legacy security architectures - VPNs, traditional PAM solutions, jumpboxes - all suffer from the same fundamental flaw: they were designed for a world where infrastructure lived in one data center, developers sat in one office, and software was released quarterly. That world is gone.
Today's reality is starkly different. Your infrastructure spans multiple clouds. Your developers work from everywhere. Your applications ship continuously. And now, AI agents are joining the workforce: autonomous systems that need secure access to databases, APIs, and production environments without human intervention.
The old security playbook can't handle this. Traditional PAM solutions require months to deploy, cost upward of half a million dollars annually, and still only protect a handful of critical systems. VPNs grant network access when you need resource-level control. Jumpboxes create bottlenecks and single points of failure. And none of these solutions were designed with AI agents in mind.
That's why we built the Twingate Identity Firewall.
A New Approach to Privileged Access
Twingate Identity Firewall extends Zero Trust and Privileged Access Management controls to every user, resource, and agent in your organization, regardless of where they work. It unifies network access and privileged access into a single platform that's purpose-built for cloud-native, AI-powered development teams.
Here's what makes it different:
Unified Identity Enforcement
Your users authenticate once through your existing identity provider: Okta, Azure AD, Google Workspace, or any other SSO solution. That identity seamlessly passes through to every resource they access, from Kubernetes clusters to PostgreSQL databases to internal APIs. No more managing separate credentials for different systems. No more exposed public endpoints. Just identity-based access, everywhere.
Dynamic Zero-Standing Access
Access is granted just-in-time, based on identity, device posture, location, and contextual signals. Users and agents get exactly the permissions they need for exactly as long as they need them, then those permissions automatically disappear. Such ephemeral access dramatically reduces your attack surface without the friction of manual approval workflows or support tickets.
Complete Visibility and Control
Every command, every API call, every database query is tied to a specific user or agent with forensic-level detail. Session replay capabilities let you see exactly what happened during any access session. You need visibility for compliance, incident response, security operations, and knowledge sharing. You don’t need additional overhead.
Cost-Effective Scale
Deploy comprehensive privileged access controls across your entire environment at a fraction of traditional costs. Until now, the cost of expensive, duplicative controls makes protecting non-administrative users prohibitively expensive. No hardware appliances or complex infrastructure requirements. Just software that works for you.
Built for the Age of AI
AI is fundamentally changing how software gets built. Developers are using AI coding assistants that need access to codebases and deployment pipelines. AI agents are performing tasks that previously required human intervention, from infrastructure provisioning to data analysis to incident response. These agents need secure, identity-based access just like human users.
Twingate Identity Firewall is purpose-built for this agentic future. It extends the same Zero Trust principles to AI agents that you apply to human users, with planned support for emerging standards like the Model Context Protocol (MCP) and Agent-to-Agent (A2A) communication. This means your AI agents can work autonomously without compromising security.
We are on a mission: Our customers are building the AI infrastructure that will power a new tomorrow. Ophir Zahavi, Senior Cloud Engineering Manager at H2O.ai, puts it this way:
"At H2O.ai, we're all about democratizing AI. Twingate is a natural extension of that philosophy. It's the path of least resistance to least privilege access, allowing our globally distributed teams to get just-in-time access to what they need—whether it's an API, a Kubernetes cluster, or a Postgres database—without compromising our zero trust principles. It's security that truly enables developer speed at the scale we need for AI."
Like H2O.ai's approach to AI, we're looking to democratize privileged access.
Simplicity at Scale
The most powerful feature of Twingate Identity Firewall might be what it removes from your infrastructure. No jumpboxes to maintain. No VPN concentrators to scale. No complex firewall rule management. No manual credential rotation. No per-resource configuration overhead.
Deployment takes minutes instead of months. You connect Twingate to your identity provider, deploy lightweight connectors in your environments (they run anywhere: cloud VPCs, on-premises networks, Kubernetes clusters), and define access policies. That's it.
Because Twingate integrates natively with modern DevOps workflows, including infrastructure-as-code tools like Terraform and Pulumi, you can manage access policies the same way you manage infrastructure. API-first design means everything can be automated. And because access decisions happen before network traffic ever leaves a user's device, unauthorized access attempts never even reach your resources.
The result? Security teams get the granular control and visibility they need. Developers get fast, frictionless access to the resources they need. And IT teams finally get to sunset those legacy VPNs.
Getting Started
Twingate Identity Firewall is available now and works seamlessly with Twingate Private Access and Twingate Internet Security. Current support includes Kubernetes API and SSH. PostgreSQL and HTTPS sessions, with expanded protocol support and specific enhancements for Model Context Protocol (MCP) and Agent-to-Agent (A2A) workflows, are coming soon.
Organizations can start free with the Twingate Starter Plan, which includes Identity Firewall for up to 5 resources with no credit card required. From there, scaling to thousands of resources and users is just as simple.
The old trade-offs are over. You don't have to choose between security, performance, and simplicity anymore.
You can have all three.

New to Twingate? You can try out Twingate for free or request a personalized demo from our team.
Solutions
Solutions
The VPN replacement your workforce will love.
Solutions